
Capture in Random Access Networks
The name 'capture effect' was originally used to describe the effect of the threshold in
analogue non-linear modulation (such as FM). In studies of collision-type random-
access networks for data communication, the description 'capture effect' has been adopted
to describe the fact that any practical radio receiver may successfully receive a message, despite the presence of interference from other (weaker) signals.
If packets compete for successful reception at the
receiver, one signal may 'capture' the receiver. In this context, however, the word
'effect' has lost its meaning of indicating a remarkably rapid impairment of the quality of
reception with only a slight decrease of the C/I-ratio.
In network planning, but also in many studies into the performance of wireless networks, a receiver threshold or protection ratio is considered.
The performance of random-access protocols strongly depends on the probability of a
successful transmission of an individual data packet over the common radio channel.
We can make a subtle distinction between receiver capture and successful reception. With receiver 'capture' we typically mean that a strong signal dominates the decision variables in the receiver detector.
Despite such receiver capture, the signal may nonetheless contain bit errors that incidentally leads for failure of correct packet detection.
The probability of successful reception
depends on
In theoretical analyses, basically two classes of models
exist:
- Models that focus on channel aspects: It is assumed that successful reception occurs
if (and only if) a limited number of conditions are fulfilled, under which capture is
likely to occur. Mostly, received signal powers are considered as the criterion for
capture. In these models, the probability of bit errors and the effect of coding are not
addressed explicitly.
- Models focusing at the detection process in the receiver: These models allow investigation of the
probability of success, erasure or undetected error during a particular time slot, from
the point of view of the common receiver or a particular mobile terminal.
To confine
the complexity of the calculations, such models often simplify receiver behaviour, e.g.
by assuming perfect carrier and bit synchronisation. Such a model is acceptable if
the receiver manages to capture a signal even if the C/I ratio is small. Practical
coherent narrowband receivers, however, often fail to acquire synchronisation to a
short (burst-type) transmission if the interference is strong. In the latter case,
theoretical block success rates for perfectly synchronised detectors tend to
overestimate the probability of successful reception.
Capture Ratio Models
Examples of models that belong to former category are
- Classification of power level: Metzner proposed to intentionally divide the
participating terminals into two groups: one group employs substantially higher
transmit power than the other group. He assumed that receiver capture occurs either
if a collision involves exactly one packet from an high-power terminal and an
arbitrary number of packets from low-power terminals, or if only a packet from the
low-power group is present.
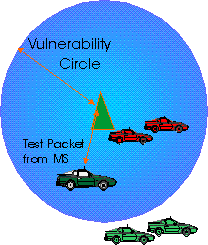
- In 1977, Abramson proposed the vulnerability circle to evaluate capture in a radio
network: A packet transmitted from distance r is received correctly if and only if no
other packet is generated within a (vulnerability) circle of radius c r, with c a system
constant.
- Kuperus and Arnbak considered a capture ratio: A packet is received correctly if
and only if its received power exceeds the joint interference power by at least a
threshold factor (or capture ratio) z. During the capture period, the received power was
considered constant. Linnartz developed a method to compute such probabilities, exploiting the properties of Laplace transforms.
- Sinha and Gupta assumed correct packet reception if the entire packet is received
during a non-fade interval. The model was considered for noise limitations
of the network performance. Linnartz studied non-fade interval for time slots with
fading interference..
- If colliding data packets arrive not exactly aligned in time, the receiver may lock on
the first arriving signal. This initiating packet is (only) received correctly if the joint
interference power that accumulates during the following vulnerable period is
sufficiently low. Packets arriving at a busy receiver are considered to be lost. For
instance, a spread-spectrum receiver may lock to an arriving packet, and effectively
reject interference from later packets.
BER Models
Models of the second category, based on bit error probabilities, are
- Receiver success for a receiver that always achieves perfect carrier and bit
synchronisation to any packet. If the number of bit errors is sufficiently small, i.e.,
smaller than or equal to the error correction (Hamming) distance, successful
reception is assumed. To obtain the probability that the receiver successfully detects a packet, one must consider the (mutually exclusive)
probabilities of success of all transmitters in the network.
- Transmitter success: Zhang, Pahlavan and Ganesh considered a receiver that
randomly selects a favourite test packet, and acquires perfect bit and carrier
synchronisation to this packet. If the test packet happens to be selected by the
receiver and detection occurs without error or with a correctable number of bit
errors, it is assumed to be received successfully.
Hybrid models
- Habbab, Kavehrad and Sundberg assumed a receiver to lock to the signal from
the nearest transmitter. If this packet is received with M or less bit errors, successful
reception is assumed.
- Sheikh, Yao and Wu considered a bit error to occur (with probability one half) if
and only if the received signal power fails to exceed the power contained in the bit of
the strongest interfering packet. Transmitter success occurs if not more than M out
of L bits are in error.
Comparison of Models
The probability of capture has to be computed for instance if one is interested in
The figure below compares several models. It shows that the results are very critical to assumptions on
the detection process in the receiver. We believe that a simple model that requires the C/I
ratio to be sufficiently large, but ignores details of bit error probabilities is fairly realistic. Results
from this model are presented by black bars.
More involved models do not necessarily yield more realistic results.
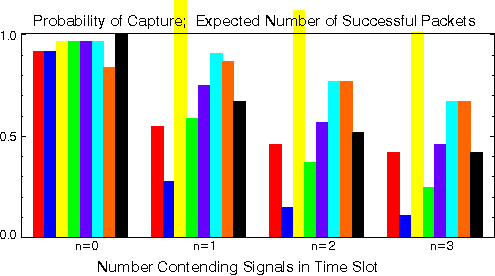
Estimates of the probability that one out of n packets successful captures the receiver
in a random access network. Packet length is taken 16 bits with BPSK modulation.
All signals are assumed to be perfectly bit aligned, and receiver bit synchronization is perfect.
- Slow fading;
- red: the receiver always synchronizes to the test packet. Note that if two packets
compete in the same slot, their phase difference may be such that the receiver could detect each of them successfully. The expected number of successfully received packets exceeds unity for n = 2.
- blue: the receiver picks one packet at random to which it synchronizes,
thus not necessarily the strongest one.
This packet captures if there are not bit errors.
-
yellow: Perfect carrier lock to one randomly chosen packet. Test packet may be strong
enough to be successful despite carrier phase differences with receiver.
- green: Perfect carrier lock to one randomly chosen packet. Differential (de)modulation
- magenta: Randomly chosen phase of the local oscillator. Note that the test
packet may nonetheless be received successfully.
- Fast fading
- light blue: the receiver always synchronizes to the test packet.
- brown: the receiver picks one packet at random to which it synchronizes,
thus not necessarily the strongest one.
This packet captures if there are not bit errors.
- Capture ratio models
- black: Successful reception occurs if the C/I ratio is above 4 dB.






 bit rate
bit rate
 type of coding, packet length
type of coding, packet length

