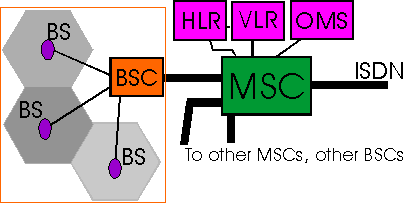

Figure: Basic Architecture of GSM
BS: Base Transceiver Station
BSC: Base Station Controller
MSC: Mobile Switching Center
HLR: Home Location Register
VLR: Visited Location Register
OMS: Operations and Maintenance Center
The Mobile Switching Center (MSC) performs the telephony switching functions for the network. It controls calls to and from other telephone and data communications networks, including the Public Switched Telephone Networks (PSTN), Integrated Services Digital Networks (ISDN), Public Land Mobile Networks (PLMN) and Public Data Networks.
The Visitor Location Register (VLR) database contains all temporary subscriber information needed by the MSC to serve visiting subscribers who are temporarily in the area of the MSC.
The Home Location Register (HLR) database stores and manages user subscriptions. It contains all permanent subscriber information including the their service profile, location information and activity status.
Security
Contributed by Bart van Rijnsoever
In GSM, security functions have been defined to protect the air interface. The security of the system depends on the tamper resistance of the Subscriber Identity Module (SIM) that is supplied to the subscriber by the operator. The SIM contains cryptographic algorithms and keys and looks like a small smart card.
Before a subscriber can use a mobile phone, his SIM is authenticated to the mobile operator. In the SIM, the authentication algorithm A3 is implemented. It is a one-way function that takes as inputs a random number generated by the operator and the secret subscriber key Ki that is stored in the SIM. The outcome of the algorithm is verified by the operator, and if it is correct the SIM has been authenticated successfully. A3 can be operator specific. To authenticate the subscriber to the SIM, a PIN-code is used. With respect to roaming and hand-over, location anonymity is achieved by the use of a temporary identification of the subscriber (TMSI).
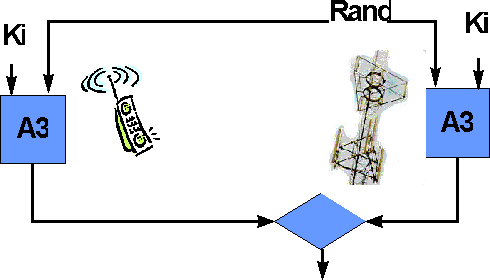
Figure: Security protocol in GSM: Authentication
Confidentiality on the air interface is achieved by scrambling on the basis of algorithm A5, that is implemented in the mobile phone and in the network. The scrambling key Kc is generated by the operator and by the SIM. Like the authentication algorithm A3, the key generation algorithm A8 takes as inputs the random number generated by the operator and the secret subscriber key Ki that is stored in the SIM.
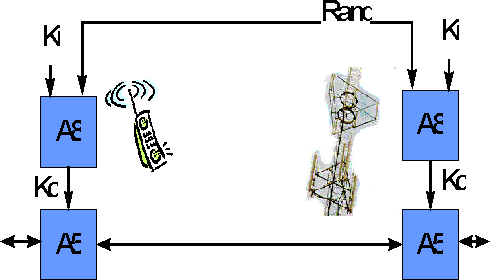
Figure: Security protocol in GSM: Confidentiality
See also our more general discussion of security in wireless communication.


