
 |
JPL's Wireless Communication Reference WebsiteChapter: Network concepts
and standards
|
One of the most efficient ways to counter fraud in mobile and other telecommunications systems is the use of cryptographic techniques.
Earlier analogue mobile systems have proved to be sensitive for sometimes severe fraud because of the lack of cryptographic protection. In many of these systems some sort of cryptographic functionality was added in a later stage to protect against ongoing fraud.
The design of new telecommunication systems recognised the importance of integrating cryptographic functions, not only to counter fraud, but also to provide additional security functions desired by the customers, such as protection against eavesdropping.
Especially new mobile, cord- and wireless telecommunication systems like GSM, DECT, TETRA and HIPERLAN offer cryptographic security functions. The integration of these functions was also catalysed by the fact that the systems were based on digital techniques and realisation was therefore easier.
The main products of ETSI are European Telecommunication Standards (ETS’s) and technical recommendations of which the European Telecommunication Reports (ETR’s) are the most important. Among other things ETSI has been responsible for drafting the standards for GSM, DECT, TETRA and HIPERLAN, which except for HIPERLAN always included a separate security part.
Within ETSI there are only two committee’s which are dealing with security only.
One of those is ETSI STAG (Security Techniques Advisory Group), which is dealing with the generic aspects of security standardisation within ETSI. For administrative reasons it was an STC but after the ETSI reorganisation it will get the status of independent TC. ETSI STAG produces several reports which are of general interest for and provide guidance to ETSI (S)TC’s.
Furthermore there is the special committee ETSI SAGE (Security Algorithms Group of Experts) which was specially set up to design and specify all the cryptographic algorithms which are part of ETSI standards. Occasionally SAGE can, with ETSI approval, carry out work for other organisations (and it has done so in the case of GSM on request of the GSM MOU).
Among the algorithms which are designed by SAGE are algorithms for GSM encryption, TE9 (multi-application smart cards) authentication and UPT (User Personal Telecommunications) authentication. Currently SAGE is designing algorithms for HIPERLAN encryption and TETRA authentication and encryption.
Of special interest is the combined STAG-SAGE work to design an encryption algorithm for operators of European public networks. It was felt by the ETSI community and especially the operators, that such an algorithm was needed to protect sensitive network management data. STAG drafted a requirements specification for this algorithm, which precisely describes and details and limits its use.
On the basis of this specification SAGE started the design of this algorithm in 1995 and will finalise this work in the second half of 1996.
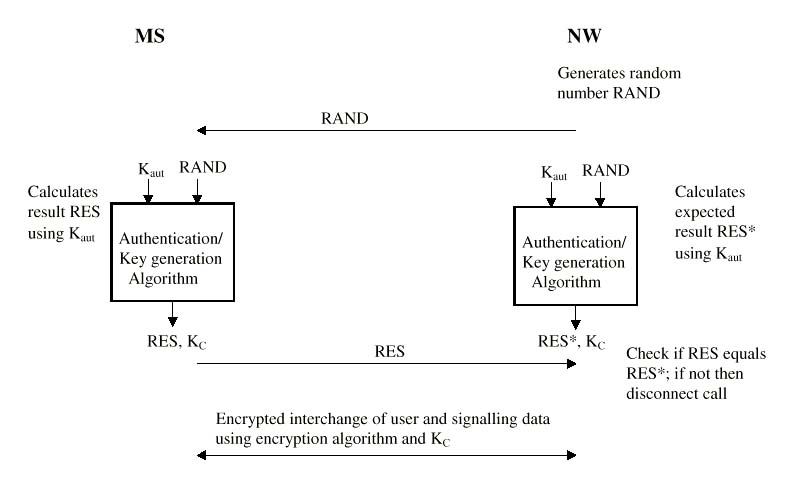
This so-called challenge signed response protocol is well known and the picture shows how an authentication key Kaut , known to the mobile station MS and the network NW only, and a cryptographic authentication algorithm are used to authenticate this MS wanting to access NW. To check if MS possesses the corresponding authentication key Kaut, NW generates a random number RAND and sends this to MS. Using its Kaut, RAND and a cryptographic authentication algorithm, MS computes a response RES and sends this to NW. In its turn NW performs a similar computation and thus obtain an expected result RES*.
NW compares the expected RES* with the RES received from MS. If these are not equal the call is disconnected.
An often used option in the challenge signed response protocol is to compute, next to the result RES, a second parameter KC which is not transmitted between the two communicating parties. If RES equals RES* the call continues and KC can be used to offer other security functions. In mobile telecommunication systems KC is mostly used to encrypt user and signalling data interchanged between MS and NW.
This principle was first used in GSM. DECT build upon this and offered again extra security (mutual authentication of MS and NW and extended key management).
At the moment the design of TETRA is in its final stages. This system for digital Private Mobile Radio (PMR) supports features like efficient group call, fast call set up ("push to talk") and direct mobile to mobile communications (direct mode). As the system is targeted to organisations for national security and safety the provision of security functions is even more important than in the case of GSM and DECT.
The TETRA security is based on the DECT security with a number of security features added. The result is that TETRA offers the following security features
To support the TETRA security two standard encryption algorithms and one standard authentication algorithm will be specified by ETSI SAGE.
Independent of this HIPERLAN defined its security. Only an encryption mechanism is specified. Explicit authentication and key management have been, until now, outside the scope of the standard. There will be one standard encryption algorithm specified by SAGE for general use.
The increased difficulty for legal interception is of growing concern for many national authorities.
In recent years there has been much effort to find the balance between offering the desired security to users, service providers and operators of telecommunication services and the requirements from national authorities with respect to legal interception.
On a technical level this has been done by introducing a new concept called Trusted Third Parties (TTP’s) which supports the security key management and among other things can act as a trusted intermediate between a secured telecommunication system and a national authority.
Originally TTP’s were use as trusted intermediate for communications in electronic commerce (an electronic notary so to say). However it is now more and more being recognised that they can also support key escrow, which in practice means making available key to lawful interception agencies which have a legal warrant.
At the moment the are several initiatives, e.g. from ISO, ETSI STAG and the European Commission’s INFOSEC programme on the (pre) standardisation of TTP’s which recognise its use for key escrow.
 Enrique
Areizaga of ROBOTIKER (SPAIN) discusses the Security of Bluetooth and
other wireless networks. MP3 files: 1,
2, 3,
4, 5
Enrique
Areizaga of ROBOTIKER (SPAIN) discusses the Security of Bluetooth and
other wireless networks. MP3 files: 1,
2, 3,
4, 5



![]()
JPL's Wireless Communication Reference Website
© Gert Roelofsen, 1999.