
 |
Wireless CommunicationChapter: Network Concepts and Standards, 802.11 WLAN |
contributed by Paul Vrancken, CoSiNe, Philips Research
The
802.11 work groupís charter is to develop Physical layer and MAC sub-layer specifications
for wireless Local Area Networks (LANs) carried out under Project Authorization
Requests (PAR) approved by the IEEE Standards Board and assigned to 802.11 work
group (WG). Individual standards activities within 802.11 WG are carried out
by Task Groups (TG). These Task Groups within the 802.11 Working Group work
on the specifications, seeking to develop the highest quality interoperable
standards for wireless Internet. These specifications focus on improving service
levels and resolving compatibility issues between manufacturers of wireless
LAN equipment. Since the initial establishment of the 802.11 standard working
group, it has been extended with numerous task groups, designated by letters.
Some groups have completed their tasks, and the results have been added to the
original standards. The details of each task group are listed below. Note that
many TG are still under PAR and thus subject to change.
The IEEE 802.11a Physical
Layer (PHY) is the layer closest to the media in the OSI stack. The PHY
provides the connection between the MAC and the wireless media. The physical
layer consists of two sub layers, the PLCP and the
PMD. IEEE 802.11a and b use
the same MAC but differ in the PHY. The reason is that IEEE 802.11a uses a
technique called Orthogonal Frequency Division Multiplexing (OFDM) while IEEE
802.11b uses the High Rate Direct Sequence Spread Spectrum (DSSS) system for
transmission in the wireless medium. The available data rates
are 6, 9, 12, 18, 24, 36, 48, and 54 Mbps where the support of transmitting and
receiving at data rates of 6, 12, and 24 Mbps is mandatory. The system uses 52 sub carriers
that are modulated using binary or quadrature phase shift keying (BPSK/QPSK),
16-quadrature amplitude modulation (QAM), or 64-QAM.
OFDM therefore improves the WLAN capacity and data
rates up to 54 Mb/s can be achieved.
The IEEE 802.11b Physical Layer (PHY) is the layer closest to the media in the OSI stack. The PHY provides the connection between the MAC and the wireless media. The physical layer consists of two sub layers, the PLCP and the PMD. As mentioned IEEE 802.11a and b use the same MAC but differ in the PHY. The reason is that IEEE 802.11a uses a technique called Orthogonal Frequency Division Multiplexing (OFDM) while IEEE 802.11b uses the High Rate Direct Sequence Spread Spectrum (DSSS) system for transmission in the wireless medium. 802.11b defines two higher data rates of 5.5 and 11Mbps. The changes in the physical layer to support these two data rates only affect the DSSS PHY layer since FHSS cannot support these data rates.
The chip sequence and the coding technique are different than the ones used for 1 Mbps and 2 Mbps data rate. The 11-chip Barker code is replaced by 64 8-chip codes using complementary code keying. The long PLCP preamble which has to be transmitted at 1 Mbps according to the original IEEE 802.11 incurred an important overhead for DSSS systems faster than 1 Mbps. 802.11b provides an optional mode which uses a shorter preamble to lessen the overhead.
This supplement to ISO/IEC 10038 (IEEE 802.1D) adds a
sub clause under 2.5 Support of the Internal Sub-Layer Service by specific MAC
Procedures to cover bridge operation with IEEE 802.11 MAC.
This supplement defines the physical layer
requirements (channelization, hopping patterns), new values for current MIB
attributes, and other requirements to extend the operation of 802.11 WLANs to
new regulatory domains (countries).
Quality of service
(QoS) demands guaranteed constant bit rate channel allocations with a constant delay and
minimum jitter. The original 802.11 media access control protocol was designed
with two modes of communication for wireless stations. The first, Distributed
Coordination Function (DCF), is based on Carrier Sense Multiple Access with
Collision Avoidance (CSMA/CA). In CSMA/CA, once a station detects that the
medium is free it begins to decrement its backoff counter. Each station
maintains a Contention Window (CW) that is used to determine the number of slot
times a station has to wait before transmission. The backoff counter only begins
to decrease after the medium has been free for a DIFS period (DCF Inter-Frame
Space). If the back-off counter expires and the medium is still free the station
begins to transmit. In case of a collision the station randomly picks a new
back-off period from its CW, which grows in a binary exponential fashion like Ethernet,
and then attempts to gain control of the medium again. Due to collisions and the
binary backoff mechanism , there are no transmit guarantees with DCF.
An
optional second mode, Point Coordination Function (PCF), supports time-sensitive
traffic flows. Wireless access points periodically send beacon frames to
communicate network identification and management parameters specific to the
wireless network. Between the sending of beacon frames, PCF splits the time
into a contention-free period and a contention period. With PCF enabled, a
station can transmit data during contention-free polling periods. However, PCF
hasn't been implemented widely because the technology's transmission times are
unpredictable.
It can be seen from the basic DCF mechanism above, that at least two
parameters can be used to provide channel access differentiation: the defer
time DIFS and CW, based on
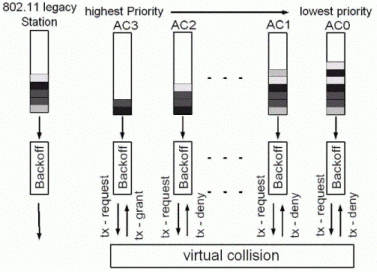
On
this mechanism EDCF
is also developed; instead of treating all traffic with a single DIFS value and
a single (CWmin, CWmax) set, EDCF defines that the channel access has up to
eight Access Categories (AC), each with its own Defer Time called Arbitrary
Distributed Inter-Frame Space (AIFS) and CWmin/CWmax values. According to the
draft, one or more user priorities can be assigned to one AC and normally
packets belonging to the same priority share one buffering queue. This implies
that no
guarantees of service are provided, but EDCF essentially establishes a probabilistic
priority mechanism to allocate bandwidth based on traffic categories.
Multiple instances of
this
enhanced variant of DCF shall be running simultaneously in each STA. Therefore,
there exist two levels of channel access contention: internal contention among
traffic of different priorities inside the same STA and external contention
among traffic from different STAs. Collisions may happen at both levels and are
resolved similarly such that higher priority traffic will most probably obtain
the channel first and lower priority traffic will have to back off. Summarizing:
different values of defer timer and back off timer are used to enable
prioritized channel access for different types of traffic.
IEEE P802.11 specifies the MAC and PHY
layers of a Wireless LAN system and includes the basic architecture of such
systems, including the concepts of Access Points and Distribution Systems.
Implementation of these concepts where purposely not defined by P802.11 because
there are many ways to create a Wireless LAN system. Additionally many of the possible
implementation approaches involve concepts from higher network layers. While
this leaves great flexibility in Distributions System and Access Point
functional design, the associated cost is that physical Access Point devices
from different vendors are unlikely to inter-operate across a Distribution
System due to the different approaches taken to Distribution System design.
This recommendation specifies the
necessary information that needs to be exchanged between Access Points to
support the P802.11 DS functions. The information exchanges required is
specified for, one or more Distribution Systems; in a manner sufficient to
enable the implementation of Distribution Systems containing Access Points from
different vendors, which adhere to the recommended practices.
The IEEE 802.11g further enhances the Physical layer's modulation technique. It adopts the modulation scheme used by both IEEE 802.11b and IEEE 802.11a. For 802.11b compatibility, 802.11g incorporates 802.11b's Complementary Code Keying (CCK) to achieve bit transfer rates of 5.5 and 11Mbps in the 2.4Ghz band. In addition, 802.11g adopts 802.11a's Orthogonal Frequency Division Multiplexing (OFDM) for 54Mbps speeds but in the 2.4Ghz range.
802.11g also comes with a pair of optional, and incompatible, modes to achieve throughput ranges in the 22Mbps range. These are Intersil's CCK-OFDM mode with a maximum throughput of 33Mbps and TI's Packet Binary Convolutional Coding (PBCC-22), with a throughput range of 6 to 54Mbps.
European
radio regulations requires radio local area networks (RLANs) operating in
the 5 GHz band to use transmit power control, involving specification of a
regulatory maximum transmit power and a mitigation requirement for each allowed
channel, to reduce interference with satellite services. The TCP service is
used to satisfy this regulatory requirement.
The TPC service provides for
the following:
Association of STAs with an
access point (AP) in a basic service set (BBS) based on the STAs power
capability
Specification of regulatory
and local transmit power levels for the current channel
Selection of a transmit power
for each transmission in a channel within constraints imposed by regulatory
requirements
Adaptation of transmit-power
based on a range of information, including path loss and link margin estimates.
Furthermore,
European radio regulations requires radio local area networks (RLANs) operating in
the 5 GHz band to implement a mechanism to avoid co-channel operation with
radar systems and to ensure the uniform utilization of available channels. The
DFS service is used to satisfy this regulatory requirement.
The DFS service provides for the following:
Association of STAs with an
AP in a BSS based on the STAsí supported channels.
Quieting the current channel
so it can be tested for the presence of radar with less interference from other
STAs.
Testing channels for radar
before using a channel and while operating in a channel.
Discontinuing operations
after detecting radar in the current channel to avoid interference with radar.
Detecting radar in the
current and other channels, based on regulatory requirements.
Requesting and reporting of
measurements in the current and other channels.
Selecting and advertising a
new channel to assist the migration of a BSS or independent BSS (IBSS) after
radar is detected.
Along with meeting regulatory requirements, DFS and TPC can be used to improve the management, deployment and operation of WLANs.
802.11i is a standard from the IEEE 802.11i committee that aims to solve the security flaws that haunt the 802.11a and 802.11b wireless networking standards. With wireless networks (such as 802.11b) becoming increasingly popular and the WEP (Wireless Equivalence Privacy standard, the current security standard) being exposed several times to flaws, the current wireless networks are vulnerable to hackers located within range. 802.11i addresses this problem by providing for better security with difficult to break encryption techniques and algorithms.
802.11i architecture
The 802.11i Security has a frame work based on RSN (Robust Security Mechanism). RSN consists of two parts:
The Data Privacy Mechanism
Security Association Management.
The Data Privacy Mechanism supports two proposed schemes: TKIP and AES. TKIP (Temporal Key Integrity) is a short-term solution that defines software patches to WEP to provide a minimally adequate level of data privacy. AES or AES-OCB (Advanced Encryption Standard and Offset Codebook) is a robust data privacy scheme and is a longer-term solution. Security Association Management is addressed by
a) RSN Negotiation Procedures
b) IEEE 802.1x Authentication and
c) IEEE 802.1x Key management
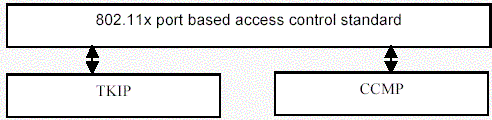
The 802.11i specification can be viewed as three modules in two layers. Encryption algorithms form the lower layer with TKIP and CCMP. Above the encryption algorithms is the 802.11x, which is a port based access control standard. The three modules work together to form the security system.
The key features of 802.11i are:
Supports two encryption standards
Encryption based on AES (Advanced Encryption Standard) with 128-bit strong key cipher
TKIP encryption
CBC-MAC cipher algorithm (CCMP) handles header and data integrity
Change in cipher keys over time
EAP (Extensible Authentication Protocol) for key management
Advanced Encryption Standard is a symmetric iterated block cipher (uses the same key for both encryption and decryption). The algorithm makes multiple passes over the input data and outputs fixed length blocks. The AES algorithm in 802.11i uses a 128-bit encryption key. This AES based encryption standard is mandatory for 802.11i devices.
TKIP is an encryption standard designed to address all known vulnerabilities in the existing wireless standards while maintaining backward compatibility. The key features of TKIP include:
TKIP is optional in 802.11i devices but provides increased security and privacy when used.
802.11i Standard Operational Phases (SOP)
The Standard Operational Phases of a 802.11i based network client are as follows:
The client and access-point exchange messages for capability identification
Access-point advertises its authentication capabilities to the client
Authentication is performed producing a master key (MK) that exists between the client and the authentication server.
A pair wise master key (PMK) is created from the master key for use by the client and the access-point. Also the Temporal key (TK) is created that is actually used to secure data communications between client and the access-point
Enhance
the 802.11 standard and amendments, to add channel selection for 4.9 GHz and 5
GHz in Japan to additionally conform to the Japanese rules for radio operation.
The
goal of 802.11K is to create a Radio Resource Measurement (RRM) standard that will
enable interoperable solutions for the sensing, characterizing, reacting, and
adapting to WLAN signal conditions. This will result in more efficient and
secure WLANs with higher quality of service (QoS).
The original standard has a basic set of radio resource measurements for internal use only. These measurements and others are required to provide services; such as roaming, coexistence, and others; to external entities. It is necessary to provide these measurements and other information in order to manage these services from an external source.
802.11K
is a pending, not yet ratified IEEE 802.11 standard that will define
measurements and develop mechanisms to provide 802.11 wireless network
measurement information to higher layers and new applications. The resultant
standardized RRM information will enable improved management and better service
for the mobile enterprise user.
Systems
are increasingly mobile through the use of cellular and 802.11 WLAN technology.
This has resulted in the need to know the location of wireless devices, the
nature of their radio coverage, and their identity. In addition, as Voice Over
IP (VOIP) becomes more widespread, the requirement to provide Enhanced 911
(E911) service is critical. Voice communications like VOIP also imposes QoS
(quality of service) requirements.
Information about ports, access points (APs), wireless link capabilities,
radio signal strength, and signal to noise ratios and other QoS metrics are
issues that concern the 802.11K working group. As always, in 802.11
specifications, vendor interoperability will be a key focus of 802.11K.
802.11K
is significant because it indicates a maturing WLAN industry that is now
beginning to focus on WLAN management issues. It recognizes that to manage
mobile enterprise systems there is a requirement for common data measurement and
management based on that measurement. The 802.11 standards have given us WLANs
that work. The goal of 802.11K is now to make wireless LANs reliable, available,
and maintainable
Task Group "Letter - L" not to
be used by the IEEE 802.11 Working Group for inclusion into the published
standard due to possible confusion with 802.11i.
Maintenance of technical and editorial corrections to
the 802.11-1999 Wireless LAN Medium Access Control (MAC) and
Physical Layer (PHY) specifications standard.
Task Group N (TGn) is chartered to define "high throughput" speeds for wireless networks. The goal is a speed of at least 100 Megabits per second (Mbps) of actual throughput. This is not just the data-rate, which could be substantially higher. The two major competing proposals are TGn Sync and WwiSE.
TG nSynch, led by Atheros with Intel, Matsushita, Philips and Sony as members, is combining MIMO (multiple in, multiple out antennas) with single and double-wide channel allotments of 20 and 40 MHz. With 40 MHz of spectrum and eight antennas (four transmit, four receive), they expect to reach 500 Mbps of raw throughput. In 5 GHz, Agere says, they could have 11 double-wide channels, while two are possible side-by-side in 2.4 GHz. Agere's proposal appears entirely backwards compatible with the single-wide, 802.11b/g channel and 2.4 GHz compatibility as a baseline.
Airgo leads a faction called the World Wide Spectrum Efficiency (WWiSE) group, which favours sticking with the 20MHz bandwidth and using advanced coding techniques and MIMO antennas.
A proposed IEEE task group to be spun out of the 802.11i group that will focus on a standard for a fast handoff that is fully secure and compatible with 802.11i and WPA. Handover between different access points within the building as callers move between them. The roaming is supported in existing WiFi, however, causes a brief break in the data stream. This is insignificant to data traffic, but unacceptable for voice calls. The upcoming 802.11i standard exacerbates the situation by extending the handover time (up to70 milliseconds) which makes voice calls impossible.
The purpose of the proposed project is to amend the existing IEEE 802.11 standard to make it suitable for interoperable communications to and between vehicles. The primary reasons for this amendment include the unique transport environments, and the very short latencies required (some applications must complete multiple data exchanges within 4 to 50ms).
The IEEE 802.1Q standard defines the operation of VLAN Bridges that permit
the definition, operation and administration of Virtual LAN topologies within a
Bridged LAN infrastructure. The IEEE's 802.1Q standard was developed to address
the problem of how to break large networks into smaller parts so broadcast and
multicast traffic would not grab more bandwidth than necessary.
The Fast Roaming Task Group
will standardize MAC layer enhancements that minimize connectivity time between
a roaming WLAN unit and wired base units.†
The standard will seek to foster the use of mobile, wireless VOIP phones
and other time-sensitive WLAN applications by eliminating perceptible
disconnections as 802.11-based handsets transition from one base station to
another during a handoff.
802.11s aims to define a MAC and PHY for meshed networks that improve coverage
with no single point of failure. In such networks, 802.11 cellular WLAN access
points relay information from one to another, hop by hop, in a router-like
fashion. As you add users and access points, you add capacity. So, as in the
Internet, adding nodes becomes a scalable and redundant endeavor.


![]()
Wireless Communication
©
1993, 2004.