
 |
Wireless CommunicationChapter: Network Concepts and Standards, 802.11 WLAN |
The IEEE 802.11 MAC is the
second layer in the OSI stack. It contains functions to provide reliable data
delivery, to control the access to the shared medium and to protect the data
delivered.
The Clear Channel Assessment (CCA) is a mechanism for determining whether the medium is idle or not. The CCA includes carrier sensing and energy detection. The Carrier Sense (CS) mechanism consists of a physical CS and a virtual CS. The physical CS is provided by the PHY and is a straightforward measuring of the received signal strength of a valid 802.11 symbol. If it is above a certain level the medium is considered busy.
The virtual CS is provided by the MAC and referred
to as the Network Allocation Vector (NAV). The NAV works as an indicator for
the station when the medium will become idle the next time and is kept current
through the session duration values included in all frames. The NAV is updated
each time a valid 802.11 frame is received that is not addressed to the
receiving station, provided that the duration value is greater then the current
NAV value. By examining the NAV a station may avoid transmitting even when the
physical CS indicates an idle medium. The energy detection procedure attempts
to determine if the medium is busy by measuring the total energy a station
receives, regardless of whether it is a valid 802.11 signal or not. If the
received energy is above a certain level the medium is considered busy. The
thresholds for both carrier sense and energy detection are predefined in the
standard. For 802.11a the carrier sensitivity is 82 dBm and the energy
detection threshold is 62 dBm.
Apart from the risk of
collisions, the wireless medium is often noisy and unreliable in itself.
Therefore the MAC implements a frame exchange protocol that lets the receiver
confirm a received frame by sending an acknowledgment (ACK). In case the sender
does not get this ACK the frame is retransmitted. There are also retry counters
and time limits that restrict the lifetime of a frame, which prevents the MAC
from resending the same frame forever.
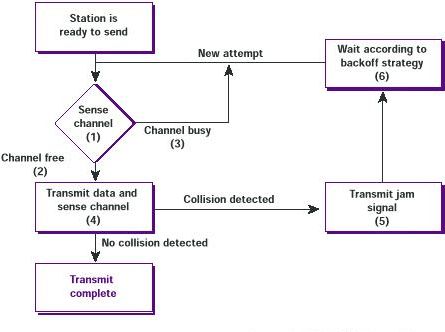
IEEE 802.11 consists of a
Distributed Coordination Function (DCF). The DCF coordinates the use of the
medium through use of CSMA/CA and timing intervals. These timing intervals are
slot time, short interframe space (SIFS), distributed interframe space (DIFS)
and extended interframe space (EIFS). SIFS and slot time are the shortest
intervals and the foundation of the others. In addition there also exists an
optional Point Coordination Function, which is not considered here.
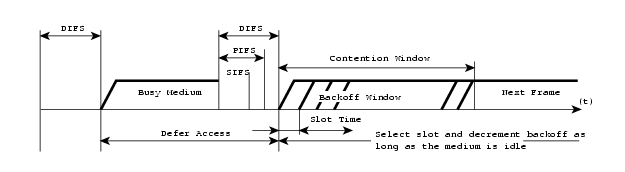
When the MAC receives a request for a transmission, the medium is checked by the physical and virtual CS mechanisms. If both of them indicate an idle medium for a period of DIFS or EIFS, the transmission is allowed to begin. DIFS is used after ordinary data frames and EIFS is used after detection of an erroneous frame. The SIFS is used when a station needs to keep the medium for additional transmissions like in ACK or CTS/RTS exchange and no other stations should be able to interfere.
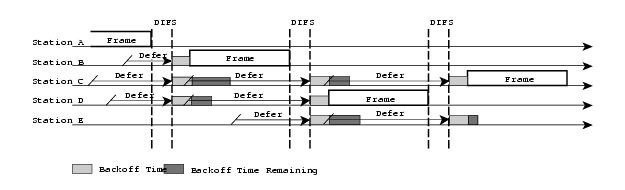
If the medium is considered busy by either
of the CS mechanisms, the MAC will choose a random
back off interval. The back off interval is a number, randomly chosen by a back
off algorithm. The number represents the amount of time the station has to sense
an idle (no transmissions) medium before it may attempt to start its
transmission again. The distribution of random numbers has a predefined range,
which is doubled with every attempt to transmit a frame until a maximum is
reached and the frame is discarded. The range of the distribution is called
Contention Window (CW). In case a frame is successfully transmitted the CW is
reduced to its minimum value. The back off number decrements each time the
medium has been free during a slot time and when the back off expires the
station can begin a transmission. It is possible for two stations to choose the
same back off interval, which will lead to a collision. Notice in the figure
that defer access is slightly longer than busy detect. The reason is that the medium
has to be free for a DIFS (or an EIFS if the previous frame was corrupted)
before the back off counter starts.
A problem with wireless systems is that every station cannot be expected to hear all other stations as in a wired network. The problem is referred to as the ``hidden node situation''. This situation occurs when stations are located such that station A cannot hear station C and vice versa, but both A and C can hear station B. Suppose then that A attempts to transmit to B. According to A's CCA, the medium is free and A begins a transmission to B. Unfortunately, the transmission cannot be received as B is occupied by decoding a transmission from C.
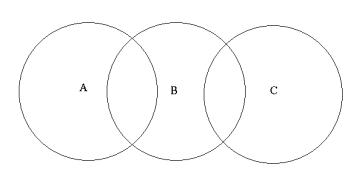
Two additional frames called Request To Send (RTS) and Clear To Send (CTS) address the problem. In this case the potential sender first requests the receiver permission to send by an RTSframe. If the potential receiver is able to receive the RTS it returns a CTSframe and the station can begin the transmission of the data frame, otherwise it cannot. All stations that receive either the RTS or the CTS will update their NAV and potential collisions can be avoided. The RTS/CTS procedure is an optional feature, which is configured to be used for packets exceeding a specified size.
The next page will give an overview of the new additions to the 802.11 standard.



![]()
Wireless Communication
©
1993, 2004.