
 |
JPL's Wireless Communication Reference Website
Chapter: Network Concepts and Standards
|
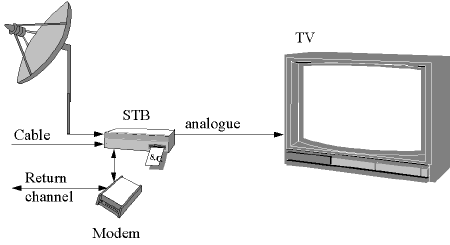
Figure 1. Basic configuration.
Nowadays, digital video services are available (e.g. DSS, DigiCipher). The digital MPEG-2 signal enters the home in encrypted form and is decrypted in the STB. After that, the clear MPEG-2 signal is decompressed and converted to an analogue signal. So the output of the STB is still analogue. This analogue signal is again protected with the Macrovision copyprotection system.
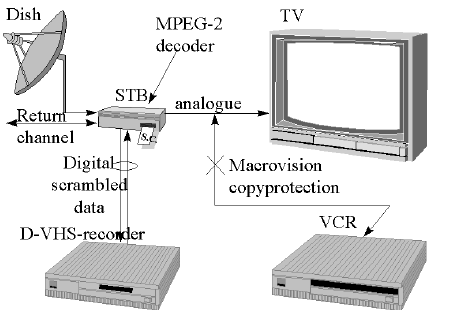
Figure 2. D-VHS recorder connected to the STB.
Digital storage devices will enter the market soon like D-VHS, DVC, etc. [23]. To record digital signals the STB must be equipped with a digital output. Actually, service providers are reluctant to accept digital interfaces and storage devices, but they may accept solutions in which the data is recorded in encrypted form to enable the basic time-shift function of the analogue VCR (Figure 2). In this case they can still control the data, because the data must still pass the STB for descrambling and is nowhere in the system available in clear digital form. However, this solution has drawbacks since EMM's can change the service keys in the smart card. Therefore, the EMM's must be skipped when the data is recorded, otherwise valid service keys can be replaced by other ones if old data containing an EMM is played back. This also means that if a STB receives a new EMM, all recorded old data is lost. Because the keys needed to descramble this data are replaced. New keymanagement strategies would be needed to support the conceptual solution of storing digital scrambled data.
The prototypes of DVB Set Top Boxes
(e.g. Nokia DVB 9500 S) are equipped with a wide range of interfaces: SCSI,
RGB, Audio analogue, RS-232, modem line and also VCR control lines [19].
This means that in the future the Set Top Box is maybe able to control
the storage device.
On this page some copy(right) protection mechanisms are described.
Using a copy protection system a consumer can not copy protected material.
If a copyright protection mechanism is used, the consumer can copy all
material, protected or not, but if such an illegal copy is found, a third
party can trace who made the copy and who the original creator of the material
was.
Macrovision exploits the automatic gain control (AGC) circuit in the
recorder. The purpose of the AGC is to adjust the level of the video signal
in such a way that the recording capabilities of the tape are fully used.
This means that weak signals are amplified and strong ones are attenuated.
Macrovision inserts some new false synchronization pulses in the non-visible
portion of the picture. These signals can make the VCR think that a perfectly
normal picture is suddenly too bright. The AGC circuit therefore darkens
it. The real picture is very dark now. The picture is varied between bright
and dark periodically in order to defeat simple eliminators that would
just simplify the dark and murky signal back to almost normal. Most TV's
are not affected, because they do not have any AGC-circuits at all. Older
VHS recorders and 8mm recorders are also not affected by Macrovision.
Several schemes of Macrovision eliminators are available. Replacing
the Macrovision pulses with a black level is one of the solutions. This
protection method can only be used for analogue recording.
The copy-prohibit-bits occur frequently in the data stream at fixed intervals. This means also that the bits can be removed easily from the data stream (set to zero).
S/PDIF is a serial one-line connection in one direction for the transport of digital stereo audio with the belonging subcode and error detection. To facilitate clock recovery from the data stream biphase-mark encoding is used. Each bit to be transmitted is represented by a symbol comprising two consecutive binary states. The first state of a symbol is always different from the second state of the previous symbol. The second state of the symbol is identical to the first if the bit to be transmitted is logical "0", however it is different if the bit is logical "1" (see Figure 3).
Preambles are specific patterns providing synchronization and identification of the subframes and blocks. These patterns violate the biphase mark code rules to avoid the possibility of data imitating the preambles. Three preambles are used (see Figure 3) to indicate the start of a sub-frame.
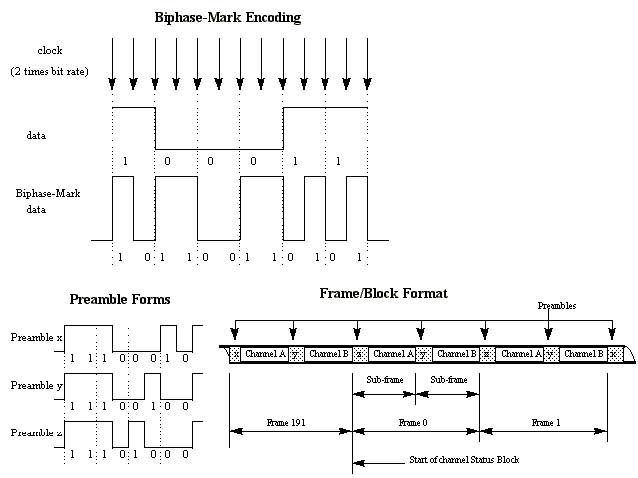
Figure 3. Biphase format, preambles and frame/block format
In this case the data on the CD is encrypted and a hardware lock or "dongle" is attached to a port on the computer. The dongle is an integrated circuit that interfaces with the application to provide de-encryption. Dongles can also perform other functions like checking for a certain serial number or code before allowing an application to run. Having the de-encryption algorithm remain in the dongle is more secure than having it remain in the memory of the computer (software approach).
All of the data on the CD-ROM that may not be copied is encrypted. The software application on the CD-ROM that uses the data is modified to de-encrypt the data (through the dongle) on the fly. Therefore, the only way to "see" (access) the data is while using the application; when someone tries to copy the data files from the CD-ROM all they will get is scrambled data. The application developer will usually modify the application so that while viewing the data the end-user can not print, save, or output the data.
Hardware locks offer some of the highest levels of security available for a CD-ROM. These dongle locks themselves cost approximately $15 each or higher, depending on the quality and quantity ordered. The application that performs the initial encryption costs anywhere from a few hundred dollars to several thousands of dollars, depending on the requirements.
One of the drawbacks to this solution is that a hardware lock (dongle) must be programmed and sent out with every disc (Multiple discs or releases can use the same hardware lock.). However, if this level of security is required, it is worth the cost.
The system can be extended by connecting the dongle with a modem to the service provider. To get a decryption key the user calls the service provider and receives the key after paying (e.g. for a pay per view event).
However, manufacturers must take into account that it is forbidden to use very strong cryptographic algorithms in consumer electronics in some countries. The law-enforcement agencies wish to have access to the communications of suspected criminals, which is threatened by secure cryptography. Industry and individual citizens, however, want to secure their private data. In the U.S. the Capstone project aims to develop a technology that attempts to balance these needs [32].
Other copy protection solutions for software involve taking an electronic "fingerprint" of the CPU or system. Then if an application is illegally moved it will not operate. In order to move the application you must un-install it then move it. This keeps applications from illegally multiplying at a customer's site. One company has even taken this idea a step further and has developed a way to put an "electronic signature" into every file on a CD-ROM. This signature is traceable and can show from who or where a file was illegally copied.
There is not much information available about this stamping method, but the number certainly will be hidden in the non-visible portion of the picture, like the Macrovision codes, teletext services etc. This means that the numbers can be stripped from the original signals. It is obvious that a similar scheme as for the Macrovision code eliminator can be used.