
Video Broadcasting Systems
Luxcrypt
Luxcrypt is used by the Dutch on RTL 4 and RTL 5 [5].
RTL 4 uses a very simple implementation of this method. It replaces the sync with
a 4 MHz burst. If you can detect the 4 MHz burst, you can put the sync back in.
RTL 5 uses a not quite so simple technique. As well as the 4 MHz burst, they invert
the video. This may be done for any random line and is harder to detect. All information
needed to de-scramble the video signal is within the decoder, so no additional
smart cards are required. There is information on the internet available to build
a complete decoder. Luxcrypt is not really a pay TV system and only works for
analogue video.
Characteristics of Luxcrypt:
| Over the air initializing |
no |
| Billing method / Interactivity |
none / no interactivity |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
no |
| Copy-protection |
no |
| Video/Audio scrambling |
removing syncs and invert video / none |
Leitch
Leitch is used by ABC, Global (Canadian) and some sporting events [6].
The video is a line renumbering scheme. The top 120 lines of the screen
are put at the bottom and vice versa, then they are renumbered in their
respective half screens. It also uses phase inversion every other line
for the color information, which is why it looks black and white. The shuffling
is done by a pseudorandom algorithm, and changes from field to field.
The color is lost because the horizontal sync is much narrower and so the
color burst is in the wrong place. Audio is 4 level encrypted PCM in the
area immediately after the narrow Horizontal Sync pulse. There are also
usually analogue audio subcarriers.
Characteristics of Leitch:
| Over the air initializing |
unknown |
| Billing method / Interactivity |
unknown / no interactivity |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
no |
| Copy-protection |
no |
| Video/Audio scrambling |
pseudorandom line shuffling / 4 level encrypted PCM |
VideoCipher: VC-1, II,
II+
Description of VideoCipher
Videocipher One (VC-I) is used by CBS and Major League Baseball [6,7,8].
Generally the audio is not scrambled, and the video is scrambled in such
a way that it looks like you are looking through a.mp3y watery screen.
VC-I uses a variable pseudorandom line delay meaning that the beginning
of each line of video occurs at a different part of the scan line. If you
squint you can almost make out the picture. The color information is not
exactly right, and the images also seem darker than normal. VC-I was the
original system proposed for HBO by M/A-Com back in the mid 1980's, but
was not adopted due to the expenses of the total system.
A sequel to VC-I is the VC-II system, the de-facto standard in the USA. The
consumer de-scramblers for VC-II are manufactured by General Instrument (GI).
Each de-scrambler contains four fixed seed keys, which are needed together which
other cycling keys to de-scramble the video. The cycling keys change every few
days and are subject to an ongoing ECM program. The service provider can switch
off a particular de-scrambler by sending an EMM, which changes the service keys
in such a way that the signal can not be descrambled using the seed keys of
that particular de-scrambler.
The Videocipher II system also offers a Pay Per View movie service.
This service is realized by connecting a modem to the de-scrambler (see
Figure) as return channel to the service provider. Somewhere in the
de-scrambler system the number of consumed Pay Per View events are counted
and stored into a RAM memory. At the end of each month the service provider
polls the de-scrambler for the number of Pay Per View purchases.
The "de-facto" standard VC-II was the world's most hacked scrambling
system. Therefore, all older VC-II decoders will be replaced by VC-II+
and forthcoming VC-II+ RS (Renewable Security) systems, which hope to thwart
this piracy through the use of a renewable smart card.
The current system employs what is called "sound in sync". The audio
portion of the program is encoded as little winky dots hidden in the sync
pulses (the bars on top or aside the screen that you do not normally see).
So the sound is digital. The real reason the sound is digital is not to
provide sound quality, but rather to insure that unauthorized reception
is not all that easy, and a decoder can not be built from scratch. No hacker
has ever build a complete new decoder, they always tamper with legal decoders.
The scrambling system uses a dual decryption key system, and is based
on the DES algorithm (making export of VC-II type decoders illegal). The
video is a simple matter to decode, as it is only video inversion and sync
suppression.
Characteristics of Videocipher II:
| Over the air initializing: |
maintain and update ACM authorizations |
| Billing method / Interactivity |
unknown / unknown |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
no |
| Copy-protection |
no |
| Video/Audio scrambling |
inversion and sync suppression / embedded in video signal
encrypted using DES |
Known hacks on the VideoCypher systems
The first of three attacks on the VCII system involved an unsuccessful
attempt to duplicate the critical proprietary IC's through the use of a
chip stripper (reverse engineering of custom IC's). Then a group euphemistically
referred to as DESUG (Data Encryption Standard Users Group) attempted to
reverse the DES (Data Encryption Standard) algorithm. This was time consuming
and it was not a valid option. The third attempt involved disassembling
the decoder control program which is stored in the system's EPROM. This
approach proved successful and lead to some major hacks on the system.
-
The first hack lead to a marketable fix. It was discovered that the pointer
could be redirected to enable decoding on all channels if at least one
channel was subscribed to and this only involved a change of from one to
six bytes, depending on the version of the VCII board. This hack was known
as the three musketeer hack (3M) because it provided all channels for the
cost of one. "One for all and all for one". The three musketeer fix was
first demonstrated in September of 1986 and it was put on the market in
December. It did not decode all services or any PPV channels. It was only
necessary to replace or reprogram the system EPROM in order to 3M a box
(decoder). The response of the decoder manufacturer was to epoxy the printed
circuit board making it harder to tamper with. Hair dryers were used to
soften the epoxy and a utility knife was used to chisel it away. During
the period from January of 1986 to December only 40,000 VCII decoders were
sold. In the first two weeks after the musketeer fix was released, another
80,000-100,000, the entire inventory of VCII's in the country were sold
and dish sales picked up again.
-
The second hack on the system involved cloning. There are 32 bytes of information
which make each decoder unique. This consists of four 7 byte seed keys
numbered from 0-3 and 4 bytes of unit ID. It was discovered that if the
unique identification information from a subscribed decoder was programmed
into an unauthorized unit, it would decode all the programming subscribed
to by the master. This meant that hundreds or even thousands of unauthorized
decoders could be cloned to receive the same programming as one decoder
which was subscribed to programming.
About a year after the introduction of the 3M chips, the "wizard" hack,
which irrevocably destroyed the system was discovered. One of the early
chips which featured this hack was aptly called Doomsday. In addition to
the 32 bytes which provides a unique identity for each VCII decoder, there
are ECM's of 28 bytes transmitted in the data stream which are critical
to the decoding function. Included is a unique service ID and channel identifier
for each channel, and a period indicator which indicates the month the
data is valid for. Seven bytes are the authorization mask which identify
which services are subscribed to. The VCII does a series of calculations
involving unit ID information and the ECM to obtain a control word (key).
It was discovered that this key was the same for all VCII's of the same
series and that this common key turned on all services except the pay-per-view
channels. The most amazing thing about the VC II system was that all non-PPV
services would be decoded if the correct working key was entered into the
correct RAM addresses, and none of the calculations mattered, and it did
not matter whether the VCII was authorized or not or even if the unit ID
data was valid. The wizard software which was developed as a result of
these discoveries calculated the working key automatically for the current
and next month. It's operation was essentially transparent to the user,though
it was necessary to enter keys for the pay-per-view movie services like
Request TV, First Choice and Action Pay-Per-View manually because their
working keys required different calculations. The keys were entered through
the keypad on the satellite receiver's remote control.
-
Somewhere in the de-scrambler system the number of consumed Pay Per View
events are counted and stored into a RAM memory. At the end of each month
the service provider polls the de-scrambler for the number of Pay Per View
purchases using a modem line.Some individuals pirate the Pay Per View service
by taking a "snapshot" of the RAM at the start of the month. They watch
all the movies they want to during the month, and then at the end of the
month they reload the data captured at the start. When the unit is polled
for Pay Per View purchases it shows none, so they are not billed.
There was an-going EMM program which was operated by G.I.(General Instrument)
after they bought out M/A-Com. When the first 3M fixes were used in 1986
it was not known that the box ID was stored in two locations. A message
was sent in the data stream to decoders to compare the ID's in both locations.
If they did not match the box was shut off. VCII's suspected of being clone
masters would be shut off on the grounds that they were oversubscribed.
Hackers monitored the datastream on certain channels and they were able
to observe EMM's being tested. This often allowed them to modify software
and hardware fixes and have the fixes ready to sell before an EMM was actually
employed.
-
One of the more amazing hacks was the Parasite board. It illustrated just
how completely the Videocipher II was understood by the hackers. It was
a Videocipher II clone built with non-proprietary components. To make it
function it was only necessary to load it with unit ID data. It was a precursor
of the SUN (Secure Universal Norm) decoder. Unlike the Videocipher II which
uses an embedded secure processor, the SUN used a detachable secure processor.
It was a plain vanilla decoder which could be programmed to emulate a VCII,
Oak, or B-MAC and it could be reprogrammed in case of a security breach.
When SUN boards were first introduced they were 2 years ahead of pirate
VCII technology. They stored two clone ID's and had wizard back up for
8 different working keys and they countered a variety of EMM's years before
they were actually employed. The only crime worse than using a Videocipher
II decoder to steal satellite delivered programming was to steal it without
using a Videocipher II decoder.
By 1992 General Instrument started to take control of its system. It established
a swap out program to issue VCII PLUS units to legitimate subscribers with
untampered decoders. Instead of a common key which turned on all services
except the PPV's each service now had its own unique working key but it
was still a common key which worked in all residential decoders. Instead
of entering a 20 digit monthly key which would turn on all the basic services,
it became necessary to enter 20 digits for each of the 60 or so channels
available. Then the keys started changing more frequently, with some changing
weekly and then daily. This led to the development of modem based fixes
which would allow the user to simply press a button on their remote control
which would cause the modem to call a BBS and download the latest working
keys into the RAM of the Videocipher board. This worked for a while but
other ECM's made it necessary to make frequent software and hardware changes.
In addition, many individuals were paying for long distance charges to
a BBS in order to download the keys. When the movie channels like HBO and
Showtime moved to the VCII PLUS system, most dishowners abandoned piracy
because they could no longer get the channels they really wanted and the
cost of piracy was higher than the cost of subscribing to the channels
which were still available.
Oak Orion
Oak Orion is used by CANCOM for the Canadian feeds and by North American
Chinese Television on K2 (maybe also by some cable companies) [6,7].
There are two types of this system. Oak sine wave and Oak Orion are very
different. Oak Orion is more like Videocipher except that included in the
Oak is an inversion bit (on one of the lines in the vertical interval)
that tell the de-scrambler to run normal or inverted video. The change from
normal to inverted is somehow related to scene changes, possibly by a trigger
based on brightness level. Sometimes it will stay in one mode for minutes
before switching to the other mode (positive or negative video).
Oak sine wave puts a big sine wave into a positive image and fools the
Horizontal sync, thus making the picture tear. Oak si wave always has audio
in the clear. Oak Orion has sound in sync just like Videocipher.
Characteristics of Oak Orion:
| Over the air initializing |
unknown |
| Billing method / Interactivity |
unknown / no interactivity |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
no |
| Copy-protection |
no |
| Video/Audio scrambling |
Videocipher like and inversion / no scrambling or like
Videocipher |
EuroCypher
The EuroCypher system was developed by the VideoCipher division, a part
of General Instrument, as an enhancement of the VideoCipher II [9].
It has been used by the British Satellite Broadcasting Ltd from March 1990
until late 1992. Today, EuroCypher is no longer in use anywhere in the
world. The access control module processes and descrambles the video signal.
There is no information available about the used scrambling method.
The main concept of access control is the concept of tiering. A tier
can be thought of as a kind of switch that, if turned on, authorizes the
Access Control Module to permit the receiver to access some service associated
with the switch. To initialize a new service, the service provider has
to make an agreement with the European Satellite Services Ltd. Once this
agreement is made, the new service is associated with a tier, and the Program
Control System controlling the service broadcasts an authenticated statement
describing which tier is needed to access the service.
Characteristics of EuroCypher:
| Over the air initialization |
maintain and update ACM authorizations |
| Billing method / Interactivity |
Post-payment / no interactivity |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
no |
| Copy-protection |
not addressed |
| Video/Audio scrambling |
unknown / unknown (maybe like videocipher II) |
Remarks: No information is available about attacks on this system by hackers.
Since the system is not in use anymore, hackers are not interested in EuroCypher.
EuroCrypt
The EuroCrypt system was developed by CCETT (France Telecom) [3,4,9].
Three kinds of informations can be broadcasted: analogue video, digital
audio and data. It was designed for MAC/PAQUET systems family. Eurocrypt
has been chosen by CSA in France for Pay-TV channels or TDF1/TDF2, by France
Telecom for Pay TV services on its cable networks and in Scandinavia by
Scansat for its ASTRA programs. The system was designed in order to permit
to be used by many service providers with minimal constraints. Several
service providers can be managed by one terminal, which is divided in independent
areas. A central authority will give different resources to each service
provider, afterward the service provider will manage their own resource
independently from the others. Each user must acquire a terminal and the
cards corresponding to each service provider. Cards must be distributed
by the service provider which keeps the propriety of the cards. The terminal
can be bought in the public market.
The EuroCrypt system makes use of a D2-MAC decoder. In this system the
video is transmitted in an analogue form and multiplexed in time with the
sound and data signals which are transmitted in digital form. At the beginning
of each video line (analogue chrominance and luminance components) a packet
of 105 bits is transmitted. This packet contains digital sound and data
(among others ECM's and EMM's). The scrambling agorithm relies on Jennings
pseudorandom generators. In case of a digital packet (sound / data) the
output bits of the pseudorandom generators are added bit by bit to the
clear data using the exclusive or operation. For the multiplex analogue
signal (video) 16 bits of the output of the pseudorandom sequence are
taken so that they determine one or two cutting points in the luminance
and chrominance spectrums. The spectrum parts obtained from these cuts,
rotate between themselves to obtain the scrambled spectrum. The key management
system works roughly as described in paragraph 2.2.
Characteristics of EuroCrypt:
| Over the air initialization: |
The entitlements for services are delivered over the air |
| Billing method / Interactivity |
not addressed / no interactivity |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
no |
| Copy-protection |
not addressed |
| Video/Audio scrambling |
double cut and rotation using PRBS / PRBSG XOR |
Remarks: EuroCrypt can be hacked by a smart card emulator. Several descriptions
and construction schemes are available on the internet.
Nagravision
Nagravision or Syster is used in France, Spain, Turkey and Germany [9].
Unlike Videocrypt and Eurocrypt, Nagravision decoder boxes are not for
sale. They are only rented out to subscribers, but still operate with a
smart card. A main problem with a working hack on the Nagra system would
be the decoders. It would be easy to replicate the pirate card, but the
decoders are not easy to get. Therefore with access to the decoders controlled
it is a very good demonstration of the philosophy of total access control.
A detachable Access Control Unit is provided to ensure security. The
DES & Public Key encryption algorithms are used in order to provide
high protection against piracy. The encoding pattern is continuously changed.
The scrambling is never the same, even on two consecutive fields, and information
about a new random pattern of encoding is sent to the decoder every second.
Encrypted data is inserted on the video signal that is read by the decoder
in order to decode the picture. Two systems are commercialized with different
(unknown) characteristics, the SYSTER and the SYSTER XP system.
Characteristics of Nagravision:
| Over the air initialization |
The entitlements for services are delivered over the air |
| Billing method / Interactivity |
not addressed / no interactivity |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
Output of demultiplexer is redirected to RS-232C port |
| Copy-protection |
not addressed |
| Video/Audio scrambling |
Shuffle Cut & Rotation (like VideoCrypt) / Spectra
inversion |
Remarks: No hacking has been reported yet, so for now it appears to be
a secure system. (Maybe this is the only secure system currently operational,
partly because the system can only be rented instead of bought).
Several software packages are available that can decode scrambled frames
without knowledge about keys etc. The frames can be decoded by using correlation
techniques to resort the scanlines. It takes about 3 minutes to decode
a frame using a 486 DX PC, so no real-time decoder can be build using these
techniques.
Videocrypt
Description and supported functions of Videocrypt
Videocrypt is a pay TV scrambling system jointly developed by Thomson Consumer
Electronics and News Datacom [5,9..12]. Over
one million users receive Videocrypt encrypted signals. It is used by British
Sky Broadcasting Channels and Asian Satellite Television Network. Videocrypt
is a multi-standard encryption system which is suitable for PAL, NTSC and
SECAM transmissions. Language is no barrier for Videocrypt with its capacity
for multi-lingual transmissions and broadcasts utilizing a comprehensive
on-screen instruction menu.
A smart card is the central key to the Videocrypt system, and the card
can be used for a variety of applications. The card is pre-coded to determine
a user requirements and it can subsequently be addressed utilizing the
decoders logic to amend the users services at the broadcasters will. The
Access Control Unit for the Videocrypt system is a removable secure processor
with memory. There is no return channel from the user to the access manager,
so the user can not ask for entitlements from his home.
There are a number of broadcasting modes which the smart card can be
used within including:
| Clear Mode |
Signals sent in the clear are recognized by the decoder
and passed to the display without further processing. |
| Free Access |
Pictures transmitted with an encryption key are delivered
directly to the display through the decoder |
| Controlled Access |
Access to encrypted pictures is determined by the level
of access authorized to the users smart card. No signals will be transmitted
in an unencrypted state without prior authorization |
Programs can be tailored to usage with the Videocrypt system and the system
offers a flexible way for pay-TV operators. There are a number of operations
mode offered as standard including:
-
Single or multiple subscriptions with many tier levels in one channel
-
Pay Per View (PPV) and impulse purchasing (see below for description)
-
Thematic selection (enable all arts programming)
-
Geographic limitation (restrict to a country/area)
-
Single-event (throwaway cards)
-
Parental Control (reception with card only)
-
Pre-determined time period
Videocrypt enables smart cards to be pre-programmed to suit the specific
programming requirements. Since there is no return channel. ordering is
performed by special offices or mail. Videocrypt can be used in a number
of applications other than TV signals protection. They include:
An existing customer would receive a new card which contains part of the
new code, the remainder of the code would be transmitted when the card
is inserted into the decoder and the subscriber compiles with the instructions
contained within the on-screen graphics.
Systems operators can now address individual subscribers, which is a vast
improvement over other scrambling systems. The operator can provide additional
services, reduce service entitlements, send individual messages, blacklist
and/or whitelist viewers.
Messages can be transmitted to individual subscribers or to a group, so
target messaging is now a potential. Messages like: "Satellite owners in
LONDON call 081 XXX XXXX now for a great bargain".
Sales over the air can be utilized with the unique identity number which
verifies an owner and their registered address. Data can be matrixed with
a user personality during ad-breaks to tailor-make the advertisement. A
unique transaction alphanumeric can be displayed on the TV screen, and
the subscriber will telephone a given number and quote the alphanumeric
- and the deal can then be completed in total security.
Characteristics of Videocrypt:
| Over the air initialization |
activate / block smart cards, address individual subscribers,
reduce service entitlements, send messages, etc. |
| Billing method / Interactivity |
buy pre-programmed card / no interactivity |
| MPEG-2 compatibility |
no, analogue system |
| PC-output |
no |
| Copy-protection |
stamping |
| Video/Audio scrambling |
PRBS (Cut & Rotation) / possibility for spectrum inversion |
Protection methods used by Videocrypt
To avoid piracy several protection mechanisms are used. Some possible attacks
are described together with the protection methods, which should prevent
such attacks.
-
Scrambling to prevent receiving data without payment:
The majority of scrambling systems currently on the market are dependent
on analogue processing circuitry, and it is a hard task to get a secure
system without picture deterioration. Videocrypt can encode and decode
a picture without degradation. The crux of the scrambling system evolves
around a patented development of Active Line Rotation (Cut and Rotate principle).
Every line of the signal is cut at a number or points along its length,
and this is chosen at random by a 60 bit pseudorandom binary sequence
generator (PRBS). As each cut point differs from the next the signal has
no viewing value to an unauthorized recipient, but authorized recipients
decoders recode the picture so that the true state of the unscrambled line
is always first out for display. The PRBS is re-seeded at times too, to
enhance the security of the system even more.
Before this ALR process can take place, the decoder needs to be aware
of the cut point on each of the transmitted lines, this is provided within
the encryption process. Each decoder utilizes an PRBS which reflects the
characteristics of the system so that the two halves can be synchronized
and a viewable picture displayed.
The Videocrypt encryption system is based around a tightly-guarded secret
which has defeated system hackers throughout the world. A final control
algorithm is central to the systems security and this can be changed at
will if the system has been hacked.
Complex calculations are performed within the system in order not to
compromise its security.
Videocrypt also has the capability of encrypting sound sources to enhance
the security of premium events. To date this level of security has not
been utilized by broadcasters. The system of spectrum inversion renders
the sounds received without authorization worthless. Videocrypt transposes
the frequencies transmitted and this in turn removed distortion of the
sound.
Nanocommands over the air can call subroutines in the smart card to
change key tables etc.
A number of steps have been taken to stop smart cards being copied or cloned.
A physical deterrent is the first line of defense, and the integrated circuit
contained within the card makes "probing" very difficult as the IC is likely
to become damaged in the process. Cost is a second factor which is likely
to deter manufacturers of illegal decoders. A considerable amount of time,
trouble and expensive resources would be required to clone the card. The
manufacturers of Videocrypt recommend that the cards are replaced every
six months, and each time this is done a "secret encrypting algorithm"
will be changed. Any pirate decoders manufactured during this time would
be relatively useless. And should a pirate decoder be manufactured, it
will contain a unique security code, which could be blacklisted by the
systems operator once the code has been discovered - leading to calls of
complaint by angry customers.
Videocrypt offers an simple method of tracking down pirates which tape
high-value programming and then distribute it. The customers unique ID
number can be hidden in the picture and retrieved by a technician at a
later stage.
-
Prevent the de-scrambler to operate without authorized smart card
The Fiat Shamir Zero Knowledge test is used to check whether a valid smart
card is inserted in the decoder or not. However, due to a programming error
on many of the original decoders and IRD's this test did not work properly.
Known hacks on the Videocrypt system
In this paragraph a historical overview is given of the most famous hacks
on the Videocrypt system.
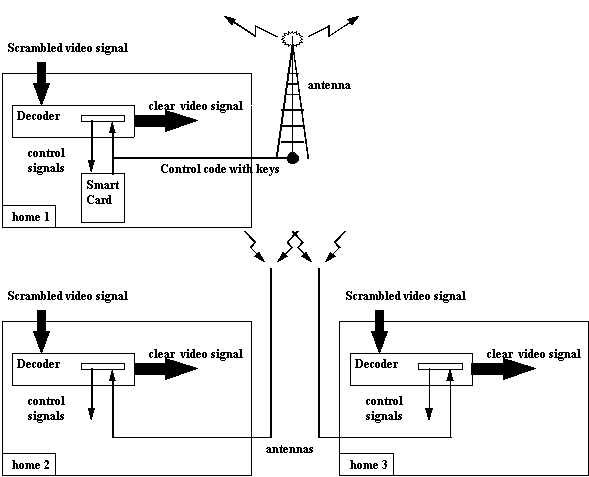
Figure 1. Mac Cormac hack.
-
Videocrypt was hacked in fifteen seconds because it contained a fundamental
flaw that was common to most smart card based systems designed in the 1980s.
The data flow between the card and the decoder could be tapped just like
a phone conversation. The data could be fed to other decoders and they
could all decode the programming from the data produced by one authorized
card. This hack is known as the McCormac Hack. It still works and
is in operation in Spain where it feeds an MMDS (multipoint micr wave distribution
system) network from one smart card (See Figure 1).
-
Another major hack on the security of the Videocrypt system was the Infinite
Lives hack. At the time, the smart cards were EPROM technology. These
cards needed 21 Volts to program them. By limiting this voltage to 12 Volts
or so, it was possible to prevent the service providers from reprogramming
or tuning off the cards. (This is a variant of the hack on the France Telecom
phone cards where the programming voltage pad was covered so that the pay
phone could not overwrite the card.)
-
The KENtucky Friend Chip was named after Ken Crouch, the head of
Sky's Security Department. The hackers had modified the program in the
IC that controlled the smart card interface. It would read the identity
of the smart card inserted in the decoder. Then it would look to see if
there was a kill message addressed to that particular card and if there
was, the modified program ensured that the kill message never reached the
card. This technique of modifying the operation of an IC in the decoder
is known as "chipping" in the USA. It was the first incident of this type
of hacking in Europe. In the DSS system, the smart card interface is controlled
by a custom microcontroller.
-
Another hack, the Ho Lee Fook hack, modified the IC that controlled
the smart card interface (like the previous hack) so that it contained
the same algorithm as the authorized smart card. Thus the first cardless
Sky Videocrypt decoder was born. News Datacom had used Fiat-Shamir's Zero
Knowledge Test and had integrated into the Videocrypt system for just such
an event. Strangely it never worked. In '93 the first piracy smart card
was developed, using a low cost PIC microcontroller manufactured by Arizona
Microchip. This is a RISC microcontroller. This card was a replacement for
the Sky's 07 card and smashed the Videocrypt system completely for approximately
one year.
-
News Datacom implemented some minor ECM's, but the hackers made new reprogrammable
cards. With a modem it was possible to transmit card updates to all European
dealers within a few hours. Some of the commercial hacks were examined
and in one case the code was extracted from one of the Ho Lee Fook chips.
The code from the 8052 microcontroller was transcoded into C. From there
it was transformed into the PC program known as Season 7 or Omigod,
an emulator program for the personal computer to drive the VideoCrypt decoder.
The distribution of this hack only took a few hours.
-
It is possible to record the scrambled video on a VCR and make a real-time
recording of the valid key data with a PC driven smart card. The same configuration
as used in the previous hack can be used. The valid key stream can then
be distributed via BBS or internet a few minutes after the programme ends.
The name of this hack is DDT or Delayed Data Transfer. This is a variant
on the Mac Cormac hack.
-
Sky switched to their new smart cards, issue 09. The previous hack stopped
working, so they thought, they won the war. The fun had only just begun.
In a month this new card was compromised by the hackers. News Datacom struck
back with another EMC, which was very difficult for the hackers to solve.
Every illegal smart card was blocked.
-
There is also a hack that can dump the programs in the smart cards. This
hack is called the Vampire hack.
-
Sky's Videocrypt system operated on an over the air authorization procedure.
Therefore if a data packet with a correct checksum was sent to a card it
would be possible to switch on cards without the intervention of Sky. The
card would not be able to tell the difference between a packet from a decoder
emulator program and the real decoder. By phoning Sky and having them turn
on some legitimate cards over the air, it was possible to build up an understanding
of how the authorization scheme worked. The program was called Phoenix.
-
Of course the program fell into the hands of commercial pirates. The Phoenix
program on its own was useful to switch on the 09 Quickstart cards that
Sky had killed. it was also being used to switch on all channels on a sky
card with only the Multichannels subscription. So, it was a Musketeer hack,
all for one and one for all. Unfortunately for the hackers, these reactivated
cards were only lasting a few days before being killed again by Sky. Sky
increased their kill cycle, so the cards only lasted a few hours.
-
The solution was a combination of the Phoenix program and a blocker for
the kill codes. This hack was called Genesis. Other hacks using the same
method were: Sunblocker, Exodus, etc. However, there was more to the Videocrypt
09 smart card than the hackers realized. The most important aspect was
that Sky could actually write to the card. The instructions for doing this
were carried in the same packets that carried the activation and deactivation
instructions. The blockers only looked for the specific number of the card
in the card socket. As long as that identity number did not appear in the
packet, it was let straight through to the card. Sky had managed to knock
out a number of cards while they were in the blockers. One of the ECMs
hit the card in a manner that effectively locked it. It was impossible
to reactivate these cards.
-
A program is available which reconstructs TV images that have been encrypted
by pay-TV broadcasting stations that use the Videocrypt encryption system.
The algorithm uses only the statistical properties of normal TV pictures
and requires NO secret information that is stored in the Videocrypt Smart
Cards or their illegal clones.
At this time, Videocrypt is still hacked. There are several working Omigod
programs available for the PC and the MAC that can hack all of the Videocrypt
channels. These programs are free, most of the BBSes in Europe have copies.
When Sky implements an ECM, the modified versions of the programs are posted
on the BBSes within a few hours. Some pirate cards have a keypad. When
there is an ECM, the pirate card user just telephones an answering service
to retrieve a set of numbers. After entering these numbers the card operates
again. Another card uses a modem to receive the new codes. Things will
change, because Sky brings out a new 0A card. From this history it appears
that the smart cards has to be changed every six months. Otherwise it is
certain that they will be hacked.
The new protection methods have to be more complex than the existing
ones. Since the level of electronic knowledge required for hacking is high,
most hackers are technicians, engineers or at least people with a good
knowledge of electronics. Most commercial hackers work together with each
other and try to become rich by selling their pirate cards, updates and
cloned decoders. Since they make a lot of money, they are able to do big
investments in hard-ware etc.
DSS
Digital Satellite System was developed by Thomson Consumer Electronics
for the US market. News Datacom developed the conditional access system
and security encryption for DSS (and Videocrypt also described in this
chapter) equipment [7,9,13,14]. The DSS encryption
is based on the VideoCrypt access control system. It is being used by DirectTV
service as well as United States Satellite broadcasting. Now, Toshiba America,
Uniden America and Hugues Network System are also involved in DSS.
Conditional access is provided with a unique smart card for a set top
decoder.
DSS systems would use Macrovision chips in RCA and Primestar receivers
for copyprotection. All products which defeat copy protection schemes would
become illegal (copyright laws Commerce Department).
Characteristics of DSS:
| Over the air initialization |
Ability of maintaining, updating EMM authorization |
| Billing method / Interactivity |
Connection to telephone line for program initiation and
billing |
| MPEG-2 compatibility |
yes |
| PC-output |
no |
| Copy-protection |
not addressed (Macrovision?) |
| Video/Audio scrambling: |
DES / unknown |
According to information from the Hack Watch News, the DSS smart card has
been hacked and the pirate cards will enter the market in soon. However,
the plan to offer four different pirate cards with different tiers of programming
has been abandoned because it has been found that the card cannot be duplicated.
The patent number on the DSS smart card referred to the Fiat Shamir
Zero Knowledge test. It is an authentication algorithm that the decoder
runs to see that the smart card inserted in the decoder is a genuine smart
card. The same authentication algorithm is used in the analog VideoCrypt
system in Europe. There are more similarities with this older system. Anyone
trying to reverse engineer the smart card will encounter the nefarious
code 99. The card developed by RCA and Motorola can be rendered useless
by hi-frequency, low voltage, temperature and other types of probing. Any
type of tampering results in erasure of the micro code in the EEPROM and
sets the card to code 99, rendering it absolutely useless. The smart card
which has been developed for the DSS system is, at this moment in time,
impervious to all known methods of hacking. In addition, code can be reprogrammed
on-the-fly, every 29 seconds. Reprogramming was used in the 09 series smart
cards in Europe (Videocrypt) which increased their longevity, although
they eventually had to be replaced anyway.
Just as hacking the Videocipher II system never involved breaking the
DES, hacks for the DSS system do not necessarily involve being able to
reverse engineer the smart card. The fix to be released will probably involve
reprogramming the card to add existing services to those already being
paid for, including pay-per-view credits, sports etc.
DIGICIPHER I & II
The Digicipher system has been produced and commercialized by general Instrument
(GI) in its first version in 1992 [6,9]. It includes
Uplink Encoding System and Commercial Integrated Receiver/Decoder products.
PBS is using Digicipher I for its feeds to affiliates. They plan to convert
to Digicipher II when the equipment becomes available, some time in 1996.
Digicipher II uses digital transmission and is designed with an open architecture.
Only Digicipher II is here discussed.
The initial application for Digicipher II is to deliver digital television
signals by satellite and cable to subscribers. Digicipher II signals are
also transportable through micr wave, fiber, and ATM networks. Finally,
the basic digital platform is described as usable in the future for such
applications as interactive television, multimedia and HDTV. A smart card
can optionally be provided to the user if the service provider wish to
enhance the access security.
Characteristics of Digicipher:
| Over the air initialization |
It is possible to address home satellite consumers and/or
cable subscribers |
| Billing method / Interactivity |
not addressed / no interactivity |
| MPEG-2 compatibility |
yes |
| PC-output |
not addressed |
| Copy-protection |
Macrovision Copy-protection |
| Video/Audio scrambling |
DES / DES |
Remarks: For the North American C-band market, Digicipher is capable of
decoding Videocipher II+ signals. No hacking reported yet and no information
available about security.
DVB
Description of DVB
In September 1994, the major European television producers, broadcasters,
and manufacturers agreed on a new standard for the digital broadcast of
video sequences called the Digital Video Broadcast (DVB) [9,15..18].
This new technology will gradually replace the current analog PAL and SECAM
broadcast norms. The digital nature of the signals increases the quality
of the video transmission and allows the creation of new services that
were not possible before. However, these advantages come with technical
challenges are both the digital and modulation levels. DVB uses digital
technology to transmit video. The video sequences are coded using MPEG-2,
then interleaved and error coded. The Reduced Reed Solomon code may be
a candidate. The actual broadcast will be performed using the Orthogonal
Frequency Division and Multiplexing (OFDM).
The first generation of DVB consumer receivers is expected to be a set
top box called an Integrated Receiver Decoder (IRD). I.e. a small box which
contains only a receiver and the above MPEG decoder. These IRDs will have
the usual RF and SCART interfaces to the antenna, cable and TV/VCR. In
addition IRDs are expected to have also data transmission interfaces for
personal computers and other multimedia systems. One original point of
the DVB system will be that the control access module (CA) will be a separated
box which will be connected to the IRD using a PCM/CIA interface. A chip
card slot will be optionally provided on the module.
There are two proposals for the conditional access module due to the
different views of the participants. The established broadcasters, who
already offer video services, would like make sure that their investment
in their current de-scramblers is not lost. They will accept standardization
only up to a certain point. On the other hand, the newcomers, consisting
mainly of network operators and the smaller broadcasters, would like to
cooperate, since they know that not many people would buy a decoder box
to watch only one or two channels. So, complete standardization of the
module would really be the solution for them. The equipment manufacturers
also wish to standardize to come to cheap mass production.
The first proposal is now commonly known under the name of Simulcrypt.
The "newcomer" that wishes to access the "established broadcasters" set
of installed decoder boxes, first has to come to a business agreement with
the broadcaster who then ensures that his CA system also provides the newcomers
service. This means that the newcomer should deliver the scrambling keys
and the subscriber information to him, who then returns the corresponding
ECM's and EMM's and makes sure that the smart card is capable of the newcomers'
service. This proposal is heavily backed by BSkyB (British Sky Broadcasting
Channels), Canal+, Filmnet and their respective CA (Control Access Module)
system suppliers using the VideoCrypt system.
The second proposal is called Multicrypt (or Transcript?) but is better known
as the Common Interface. The Common Interface today consists of a detailed draft
specification of a standard interface between the decoder box and a detachable
module. Since the interface would have to fit all incompatible CA systems in
use today, the interface was chosen at the MPEG-2 Transport Layer. This means
that scrambled MPEG-2 data goes across the interface into the module and de-scrambled
(thus clear) data is returned, both at a rate of up to 50 Mbit/sec. The detachable
module contains the de-scrambler chip. The Common Interface is backed by the
newcomers, who see this as a fundamentally good and secure solution to the standardization
problem, it allows them to cooperate and still use their own proprietary CA
system.
Characteristics of DVB that seems to be already fixed (can change in
the future):
| Over the air initialization |
not addressed (entitlements for services, updating authorizations
etc.) |
| Billing method / Interactivity |
IRDs should include a modem for connection to a public
telephone network for access control, billing, interactive service etc. |
| MPEG-2 compatibility |
yes |
| PC-output |
yes |
| Copy-protection |
not addressed |
| Video/Audio scrambling |
own standard / own standard |
In Figure 2 a proposed scheme for the DAVIC Conditional Access system is
represented. This proposed model works with a Set Top Box implemented by
a standard terminal and a detachable CA module (PCMCIA card).
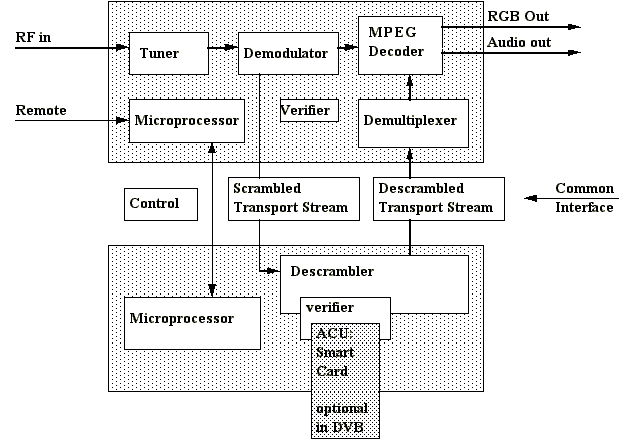
Figure 2. DVB proposal for decoder and CA system.
The questions arise if the de-scrambled stream can be tapped and if the de-scrambler
has been equipped with a digital output, which can be used for PC, multimedia
applications and a SMASH storage device.
Remarks:
-
DVB proposes to build a Near Video On Demand service. The principle consists
in transmitting simultaneously several time shifted versions of the same
program.
-
For copyright protection a watermark can be used. This solution is proposed
by the RACE ACCOPI project. A watermark must consist of a holographically
inlaid over all the picture being:
-
undeletable by a hacker
-
perceptually invisible
-
statistically invisible (cannot be deleted by filtering)
-
fully resistant to any additional noise (compression, transmission etc.)
-
Since DVB is now only at a specification stage, the system has not been
hacked.
Scrambling algorithm of DVB
The scrambling algorithm specified for common EP-DVB applications has been
designed to minimize the likelihood of piracy attack over a long period
of time. The scrambling algorithm operates on the payload of a Transport
Stream packet in the case of TSlevel scrambling. A structuring of
PES packets is used to implement PESlevel scrambling with the same
scrambling algorithm.
The PES level scrambling method requires that the PES packet header
shall not be scrambled (as required in ISO/IEC 13818-1) and Transport Stream
packets containing parts of a scrambled PES packet shall not contain an
Adaptation Field (with the exception of the Transport Stream packet containing
the end of the PES packet). The header of a scrambled PES packet shall
not span multiple Transport Stream packets. The Transport Stream packet
carrying the start of a scrambled PES packet is filled by the PES header
and the first part of the PES packet payload. In this way, the first part
of the PES packet payload is scrambled exactly as a Transport Stream packet
with a similar size payload. The remaining part of the PES packet payload
is split in super-blocks of 184 bytes. Each super-block is scrambled exactly
as a Transport Stream packet payload of 184 bytes. The end of the PES packet
payload is aligned with the end of the Transport Stream packet (as required
in ISO/IEC 13818-1) by inserting an Adaptation Field of suitable size.
If the length of the PES payload is not a multiple of 184 bytes, the last
part of the PES packet payload (from 1 to 183 bytes) is scrambled exactly
as a Transport Stream packet with a similar size payload. A schematic diagram
describing the mapping of scrambled PES packets into TS packets is given
in Figure 3.
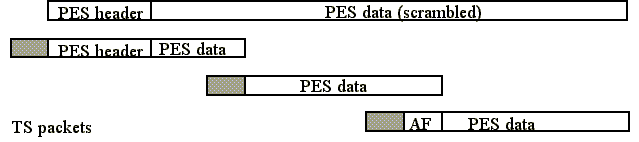
Figure 3: PES level scrambling diagram.
The PES level scrambling method puts some constraints on the multiplexing
process in order to make the descrambling process easier.
For applications that scramble MPEG-2 Sections, a problem occurs as
the MPEG-2 specified syntax does not include any scrambling control bits.
Therefore, the scrambling of Sections shall be at the Transport Stream
level and shall be signalled by the scrambling control field bits. Clear
and scrambled Sections cannot be combined in a single Transport Stream
packet. The MPEG-2 defined padding mechanism can be used to create Transport
Stream packets with only clear or only scrambled Sections. This means that
the end of a Transport Stream packet carrying a Section shall be filled
with bytes having a value of 0xFF, in order to separate clear and scrambled
Sections into different Transport Stream packets.
The algorithm is designed to minimise the amount of memory in the descrambler
circuit at the expense of the complexity in the scrambler. The exact amount
of memory and the descrambling delay depend on actual implementations.
Maximum flexibility in the operation of a broadcast infrastructure requires
scrambling to be allowed at the PES level. In order to avoid complex implementations
at the consumer receiving equipment, only a single descrambling circuit
shall be required. The DVB scrambling algorithm can scramble data with
a rate up to 54 Megabits/sec.
For more information on DVB click here.
Functionality of Set
Top Boxes in the future
The de-scrambler boxes described in the previous paragraphs are precursors
of the Set Top Box that will bring the future digital services in the home
within a few years. The de-scrambler boxes only offer TV and limited information
services. The Set Top Box of the future will offer much more services like
Teleshopping, mailbox and on-line information services, games on demand
etc.
The prototypes of DVB Set Top Boxes (e.g. Nokia DVB 9500 S) are equipped
with a wide range of interfaces (SCSI, RGB, Audio analogue, RS-232, modem
line, VCR control lines, etc.) [19]. An MPEG-2
decoder is implemented. The STB's are expected to have also data transmission
interfaces (e.g. SCSI) for personal computers and other multimedia systems.
The first prototypes do not have a digital video or audio output. This
means that only an analogue VCR can be connected to such a Set Top Box.
DVB proposed that the control access module (CA) will be a separated
box which will be connected to the STB using for example a PCM/CIA interface.
A chip card slot will be optionally provided on the module. The service
providers can implement their own proprietary CA system in this detachable
module. This means that different service providers can work with only
one Set Top Box.
It is expected that in the future all digital interfaces of the Set
Top Box will be replaced by one digital bus interface. For example a P1394
bus interface. The DVC-camcorder already has such an interface. It is questionable
if the connection to the TV is also digital. If this line is still analogue,
there must be an MPEG-decoder in the Set Top Box, otherwise the MPEG-decoder
will be implemented in a digital TV or in a PC. For sure, the Set Top Box
will have some computational power to execute for example an Electronic
Program Guide. One of the most important tasks of the Set Top Box is to
deal with conditional access and encrypted signals.








