
 |
JPL's Wireless Communication Reference Website
Chapter: Network Concepts and Standards
|
To make Pay TV services possible, each consumer needs a television, a decoder
box (Set Top Box) and a smart card, which should be plugged into the decoder
box. Since there is only a one-way communication channel from the service
provider to the consumer, no interaction of the consumer is possible. Therefore,
it is difficult for the service providers to implement services like Pay
Per View, Video on demand etc. A solution for this problem is a return
channel from the consumer to the service provider. In some existing systems
a simple modem line connected to the telephone-network is used to enable
these services (see Figure 1).
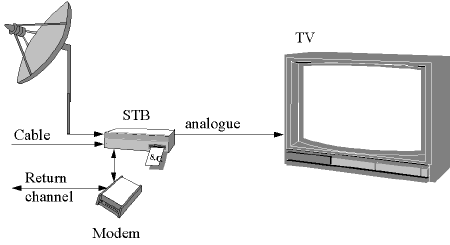
Figure 1. Basic Configuration of a Pay TV system.
Pay TV techniques rely on two independent mechanisms. Firstly, scrambling /
encryption of the picture and of the sound and secondly, management of commercial
entitlements which have to be transmitted as secured messages to the de-scrambler
box (control access).
Encryption can easily be applied on a digital bitstream. In this case, all bits are encrypted by using for example a block cipher like DES. Scrambling is used for analogue broadcasting. Using the latter method, the signal format is changed, the synchronisation signals are suppressed and separately transmitted in an encrypted form. Sometimes, the audio signal is converted to a digital signal and encrypted. This digital encrypted audio signal can be embedded in the video signal.
The data is scrambled or encrypted using a control word (CW) or key. The control word or key will change after a short period. To send the new keys to the de-scrambler ECM's (Entitlement Control Messages) and EMM's (Entitlement Management Messages) are used. Those messages have a digital signature field which ensures the integrity of the message (e.g. a HASH-code). This prevents users from modifying the context of the message.
An ECM is transmitted together with the scrambled signal. An ECM consists of three fields. The first field contains the access parameters. These parameters define the conditions under which access to the program is allowed. This field makes, for example, parental rating (additional PIN code is requested by the de-scrambler box) and geographical black out (a film may not be available in all European countries) possible. The second field contains the control word in encrypted form and the last field contains a data integrity check.
An EMM consists usually of four fields. Each EMM starts with an address field to select an individual de-scrambler box. There are two addressing modes, one for an individual de-scrambler box and one for a group of boxes. The second field contains the entitlement for the user. The third field contains the service keys in encrypted form and the last field contains a data integrity check. EMM's can also be used to send a command to the de-scrambler box (see VideoCipher and Videocrypt). Transmission of EMM's is generally the result from an explicit request from the user to the service provider. These messages are individual in general. Their content shall be interpreted by one de-scrambler box or by a limited number of de-scrambler boxes which are concerned by this particular entitlement.
EMM's do not have to be transmitted in a synchronous way with the program to which they apply. They have to be transmitted in advance in order to give access to the authorised consumer. Any network can be used to transmit them to the receiver: modem, mail or broadcast. Over air addressing means that the messages (EMM's) are broadcast.
To be sure that an EMM is received by the user, to renew a subscription for
instance, there is no other way than to repeat the message sufficiently. EMM's
are therefore organized in cycles for broadcasting. The length of the cycle
is the major parameter determining the maximum time to wait to get an entitlement
for a user, who has switched off his de-scrambler box for a long time.
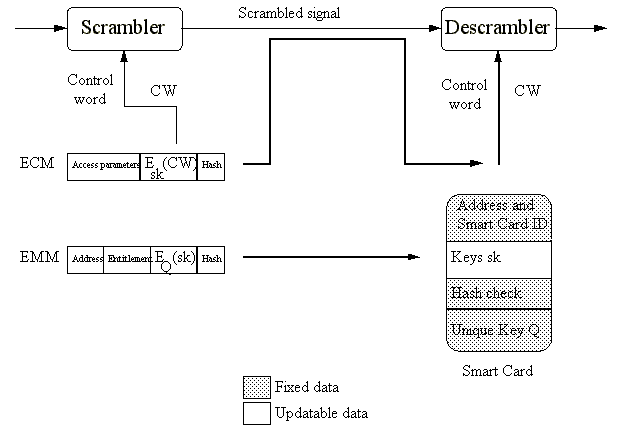
Figure 2. Key Management in a Pay TV system.
The complete key management system is represented in figure 2. The audio and video are scrambled using a cycling control word or key CW. Every fixed period (e.g. 10 seconds) an ECM is transmitted together with this scrambled signal. These ECM's contain the control words encrypted with the service keys SK, which must be present in the de-scrambler box. The service keys are less frequently updated by EMM's, for example once a month. The service keys are encrypted with one or more individual unique keys, which are safely stored inside the smart card or de-scrambler box.
The complete description of the key management system can be found in [2..4].
A main problem is that every service provider uses his own scrambling
/ encryption algorithm and key management system. This means that many
different systems are in use today.