Copyright versus right to copy.
How the struggle to protect Intellectual Property Rights
shapes the information society.
by Jean-Paul Linnartz
The introduction of the compact disc (or CD) about 15 years ago started a migration from analog to digital entertainment media. Currently, the music industry almost exclusively publishes new titles in digital form. Similarly, cellular telephony is making the transition to purely digital systems. The possibilities offered by flexible digital hardware platforms, including not only PC's but also digital decoder boxes (Set Top Boxes) and other consumer electronics products, promise sheer unlimited features and services. However, content owners face the dilemma that along with these advantages of quality, performance and functionality, digital content can be copied rapidly, perfectly, at large scale and without limitations to the number of generations. Illegal copying can be a particular threat to the Motion Picture industry, where revenues from one title are spread by the geographically and temporally phased release of the material. Typically a film is initially shown in film theaters in the U.S., followed by sales of DVD discs or tapes, lending through video rental stores and finally by television broadcasts, all in a strategically chosen sequence. Releases in other countries occur with a well-timed offset.
The example of the motion picture 'Titanic', which cost about 200 Million US dollars to produce, illustrates the amount of revenues at risks if a film stolen from a U.S. cinema appears prematurely on pirate VHS video tapes in other markets. Moreover, both in the music and film industry, a few "big hits" must compensate losses incurred on a majority of less performing titles.
While in the past home copying and piracy was regarded as an unsolvable problem, it is now being recognized as a crucial factor in the development of an information society. More and more, our economies depend on exploitation of intellectual property, so the threat of piracy may set back a healthy development of a society with a plurality of content providers with various cultural backgrounds.
The last few years have seen an enormous expansion in the number of multimedia
storage options, from ordinary CD to hot newcomers like DVD-R. The common denominator
of all these new systems is that they store and disseminate digital information,
be it text, pictures, audio, video or software. This digital nature poses a
very realistic threat to those who provide proprietary or copyrighted content.
The need for those providers to protect their legal rights has sparked a flurry
of research activity in the field of copyright protection, coming a long way
from the days of analog scrambling of premium cable-channels. The development
of the Digital Video Disk (DVD), and its recordable counterpart DVD-R, a multiply
writable DVD disk, promises up to 14 GB of storage allowing many cycles of read
and (re-) write. This triggered discussions in international fora, with participation
from the Motion Picture Association of America (MPAA), the Information Technology
(IT) sector and the consumer electronics manufacturers (CEMA) industries. Observers
see this forum as a potential trend-setter for future multimedia standards.
Copy control issues have already got on the "critical time path" of the market
introduction of many digital hardware products, including digital television
broadcasting, DVD video, the IEEE 1394 digital 'firewire' interface and improved
digital audio carriers. According to insiders, even the internal architecture
of the future PC will be heavily influenced by copy protection considerations.
Tools for copy protection in the digital world are sought in two directions:
cryptography and embedded signalling.
Cryptography
The old cryptographic paradigm in which Alice communicates with Bob and is
wiretapped by Eve, does not hold for copy protection. Rather Alice wants to
sell information to an unreliable Bob, but meanwhile she wants to restrict the
use of that content. At the same time, Bob must be able to use and copy any
similar works of art that he created himself, without any restrictions. It can
easily be understood that encryption, as for instance applied to DVD disc sectors,
only addresses part of the issue of illegal copying. It avoids that the user
has direct access to valuable, highly compressed digital content. Moreover,
the user (or more precisely his electronic device) must make use of patented
decryption algorithms to access such material. Conformance to copy protection
measures is enforced through licensing contracts. Lacking secure solutions for
copy-control over digital busses, such contracts currently state that a player
may only offer the content in analogue form to the end user.
Copy control is not the only reason why cryptography and security system design
has a growing research interest at Philips Nat.Lab. in Eindhoven While crypto
used to be the exclusive domain of national security agencies and professional
users, the information society sees a rapid growth of the use of these techniques
for pay tv, shopping over the internet, in traffic and transportation etc. As
consumer electronic products contain more and more embedded executable software,
we now have reached the point where it becomes viable to upgrade the functionality
of these devices by software downloads. Such scenarios are particularly applicable
to devices that already connect to communication networks, such as set top boxes
or cell phones. However, it does not take a great hacker to understand the security
risks associated with remotely modifiable functionality of such products. We
may not be far away from viruses in common electronic products, or one broadcaster
programming your television set such that you won't be able to zap to the channel
of a competitor.
Watermarks
Because of all the cryptographic algorithms and keys involved, the world of
playback equipment gets divided into compliant, i.e., those which use
the cryptography as for instance defined in the IEEE 1394 digital interconnect
standard, and non-compliant devices, e.g. analogue video recorders. Given
the fact that it will most likely be impossible to root out the members of the
second category, the strategy of an anti-copy mechanism should be to keep protected
content from being multiplied in the non-compliant world and hurting sales by
re-entering the compliant world.
A little math behind watermarking
The detection algorithm in its simplest
form consists of taking the inner product (denoted as · ) of the
frame J with the watermark pattern W, and this inner product
is compared with some threshold value.
Consider the watermark embedding method
of the previous section and let J be a frame. Then we define
the correlation yW(J) to be
yw(J) = W
· J.
In our and several other published methods,
the value yW(J) is then compared to a threshold value ythr(J),
which depends on (the variance of) J, to decide whether the watermark
is present in J or not. To see why this works, note that an `arbitrary'
frame I is not correlated with W, so the expectation of
W· I is zero and its variance is small.
Now if I is watermarked and the
result is J = IW, then the inner product becomes
yw(J) = W
· J = W · (I
+ W) = W · I +
W · W
Now Ew = W· W
represents the "energy" in the watermark, which generally
will be large compared to the variance of the "noise-term"
W· I. This enables reliable detection of the watermark W.
More precisely, W· I is a Gaussian random variable. In the
special case that W is randonly choosen in {-1,1}N,
the variance of W· I is proportional to Ns 2
with s 2 the variance
of the luminance of a pixel in the original image, the number of pixels
in the image. The probability Pfp of erroneously detecting
a watermark in an image without a watermark (false positive) is
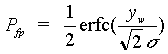
Or, for a threshold of yw
= Ew/2,
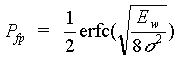
with erfc the complemenatry error function
(i.e., the area under the tail of a Gaussian probability density) and
s 2 the variance
of the luminance of a pixel in the original image.
The above expression relies on several
assumptions. One assumption is that the valuess of neighboring watermark
pixels are chosen independently. See for instance our papers at the
Data Hiding Workshop in Portland, Oregon, of April 1998 for a an analysis
of the performance under less ideal situations.
|
In order to present the content to the legal audience, it must be converted
to an analog form, for instance into an electrical current that controls the
motion of a loudspeaker cone or the modulation of a television scan line. Consequently,
video can be grabbed after Digital-to-Analog conversion and copied onto other
media as if it were the user's personal creative art work.
To address these problems, various industry consortia have come to the conclusion
that additional information must be passed along with content in an indelible
manner. This "embedded signaling" of copyright states is the second important
tool in copy control. Embedded signaling methods, also called an electronic
watermarks behave like electronic "tattoos" in that these ensure that marks
are not lost in typical signal processing operations, including format conversions.
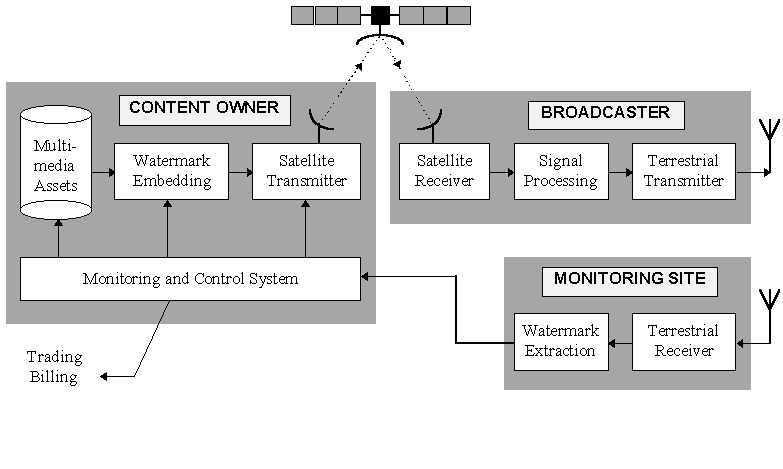 Figure: Automated television
broadcast monitoring based on embedded watermarks. A system concept that
is being developed in the Esprit Project VIVA.
Figure: Automated television
broadcast monitoring based on embedded watermarks. A system concept that
is being developed in the Esprit Project VIVA.
Besides copy control in consumer products watermarks are also used in professional
services. Nat.Lab. has teamed up with the London-based news agency WTN (World
Television News) to watermark all their material before it is disseminated to
broadcasters worldwide. The intention is to automatically monitor public and
commercial television channels at a large scale, in order to verify royalty
payments for use of news clips. Similar systems already exist for scanning the
copyrights of images posted on the internet.
Use of watermarks for copy control
A basic application of watermarking for copy control is a recorder that refuses
to make copies of watermarked, thus copyrighted content. This concept is called
record control. As hackers have sufficient facilities for tampering with
such recording devices, a preferred method is playback control. The basic
concept is that the player rather than the recorder recognizes the copy state
of the content, e.g. by detecting the watermark, and compares this with an uncopyable
physical mark on the disc. If the physical mark is correct, i.e., it is original
and matches the watermark, the device is authorised to play. This physical mark,
of course, must be such that it cannot be simulated on a recordable medium.
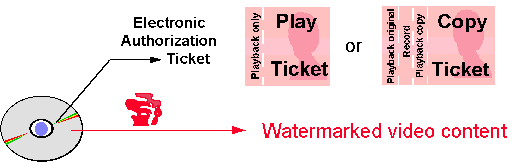
Figure: Basic elements of play control: if a player detects watermarks,
it verifies the presence of an appropriate authorisation mark.
In addition, the ticket is implemented as a cryptographic counter that can
be decremented but not incremented. This, is useful to create a copy-once functionality.
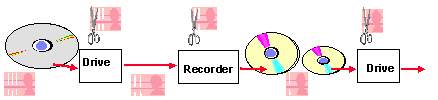
Figure 3: The ticket is clipped (cryptographically modified)
during each playback or recorder passage.
Implementation of the Watermark
A commonly used watermark embedding technique is that of making minor changes
to the luminance (i.e., the light intensity or gray level) of an image. Typically
a pseudo-noise pattern is added to a digital image, such that the modifications
are invisible for a human eye, but can be detected by dedicated hardware. To
illustrate this concept, a watermarked image, a watermark pattern and a marked
image will be available on the web.
The strength at which the watermark pattern is embedded may depend on the original
image or on local properties of the image. In areas of the image where the human
eye is sensitive to minor disturbances, it is embedded less prominently. Current
research work includes optimum detection methods, for instance exploiting redundancy
in the original image, improving robustness against modifications of the image,
and development of multimedia trading systems that use watermarking as a core
technology. Meanwhile, major efforts are undertaken to assists the development
of a legal and regulatory framework to migitate the risks of piracy and excessive
home copying associated with our current migration to an information and entertainment
society.
Concluding discussion
Protection of intellectual property is a critical aspect of the future multimedia
setting. Innovative solutions are being researched, using methods and techniques
from signal processing, human perception modeling, cryptography, network security,
systems design and many other disciplines. The outcome of these efforts and
the international regulations and standards to be drafted in the coming years
are likely to become a determining factor in our ability to introduce innovative
information and entertainment services. These depend on sound business perpectives
both for the technology and content-oriented industries.
Author:
Jean-Paul M.G. Linnartz:, Philips Research, WY8, Holstlaan 4, 5656 AA Eindhoven, The Netherlands, Tel: 040 2742302, Fax: 040 2744660, http://www.eecs.berkeley.edu/~linnartz.
The author expresses his gratitude to his collegues Geert Depovere, Ton Kalker, Maurice Maes, Joop Talstra, Jaap Haitsma and Christ Vriens, with whom he jointly developed the watermarking technology described in this paper.
JPL HOME | WATERMARKS
|
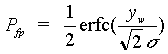
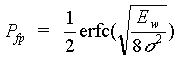
 Figure: Automated television
broadcast monitoring based on embedded watermarks. A system concept that
is being developed in the Esprit Project VIVA.
Figure: Automated television
broadcast monitoring based on embedded watermarks. A system concept that
is being developed in the Esprit Project VIVA.
